- Home
- CompTIA Security+
CompTIA Security+

SY0-501 Section 2.5 Summarize common incident response procedures
Preparation Preparing for incident response involves multiple factors. The first step is outlining how you intend to respond to specific incidents. Formulating an IRP is part of that preparation. You also will need to identify the personnel and resources needed for your response. For example, if you intend to take a server offline in the event that it is breached, do you have a backup server available? In the event of a suspected computer crime, which of your personnel are qualified to perform the initial forensic processes? If no one…

SY0-501 Section 2.4-Given a scenario, implement basic forensic procedures
The five steps outlined here will help in all incident response situations. For the exam, however, there are a number of procedures and topics about which CompTIA wants you to be aware that are relevant to a forensic investigation. We strongly recommend that you familiarize yourself with these topics as you prepare for the exam. Act in Order of Volatility When dealing with multiple issues, address them in order of volatility (OOV); always deal with the most volatile first. Volatility can be thought of as the amount of time that…
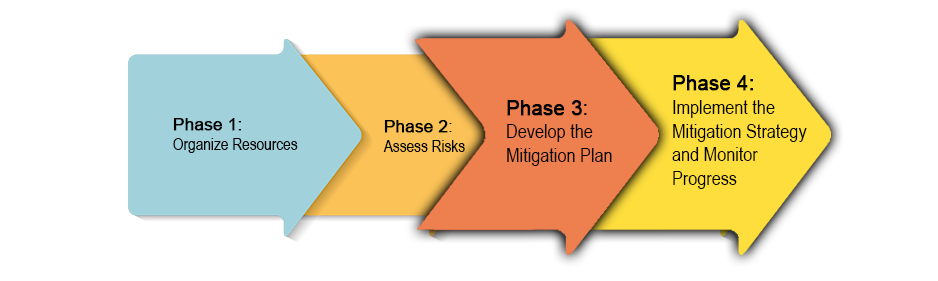
SY0-501 Section 2.3 Given a scenario, implement appropriate risk mitigation strategies.
The selection and specification of security controls for an information system is accomplished as part of an organization-wide information security program that involves the management of organizational risk—that is, the risk to the organization or to individuals associated with the operation of an information system. The management of organizational risk is a key element in the organization’s information security program and provides an effective framework for selecting the appropriate security controls for an information system- –the security controls necessary to protect individuals and the operations and assets of the organization….
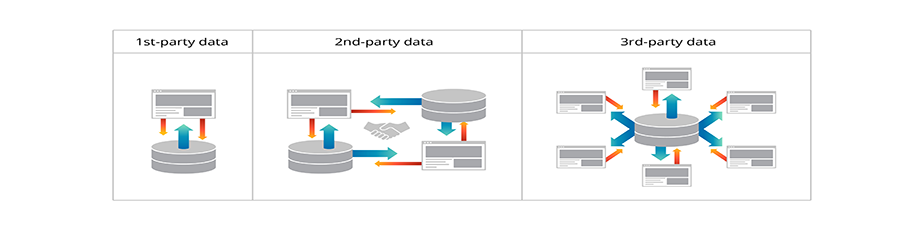
On-boarding/off-boarding business partners Transitioning with a business partner occurs either during the on-boarding or off-boarding of a business partner. Both the initialization and the termination of a close business relationship have serious security issues. During the on boarding of a new business partner, it is important to determine whether the security policies of both organizations are compatible, at least in areas where the two companies’ networks will interact. One area that usually does get adequate attention from most companies is the issue of interoperability agreements. These are documents that define…

SY0-501 Section 2.1-Explain the importance of risk related concepts.
Control types To prepare for the certification exam, it often helps to use analogies to put topics in con- text. In light of that, consider a residential home this author owns in the middle of town. I grow prized tomato plants in the backyard, and it is very important to me that no one goes back there for fear that they might do something to harm the tomatoes. Thus, I implement the following controls: Administrative: I establish a number of policies to keep the tomatoes safe: Preventive: I instruct every…
SY0-501 Section 1.3 – Explain network design elements and components.
DMZ In computer networking, DMZ is a firewall configuration for securing local area networks (LANs). In a DMZ configuration, most computers on the LAN run behind a firewall connected to a public network like the Internet. One or more computers also run outside the firewall, in the DMZ. Those computers on the outside intercept traffic and broker requests for the rest of the LAN, adding an extra layer of protection for computers behind the firewall. Traditional DMZs allow computers behind the firewall to initiate requests outbound to the DMZ. Computers in…

SY0-501 Section 1.2 Given a scenario, use secures network administration principles.
Rule-based management Traditional network management systems are implemented in a rules-based environment. Here, the functional areas of network management are performed based on a set of guidelines established by the administrative staff. Fault events, configuration setup, accounting recording, performance thresholds and security rules are all preset, based on best practices. One advantage of rules-based implementations is that the interaction between the managed device (agent) and the manager can be simplified to a very small set of actions. In the simplest case the agent responds to polls from the manager and…

This is no different from our daily lives. We constantly make decisions about what risks we’re willing to accept. When we get in a car and drive to work, there’s a certain risk that we’re taking. It’s possible that something completely out of control will cause us to become part of an accident on the highway. When we get on an airplane, we’re accepting the level of risk involved as the price of convenience. However, most people have a mental picture of what an acceptable risk is, and won’t go…



