Use VCE Exam Simulator to open VCE files

This Chapter covers following Topic Lessons
This Chapter covers following Lab Exercises
In this chapter we will add Resource Group, Tags and Locks to the Topology. We will create Azure policy at Resource Group level.
Resource Groups are logical containers in which resources are grouped. All Resources in Azure are created in Resource Group. Resource Group can be created independently or can be created along with resource creation.
Resource groups allow you to manage related resources as a single unit. Using Resources Groups you can monitor, control access and manage billing for resources that are required to run an application.
In Azure Portal click Resource groups in left pane>Click +Add>Add Resource Group blade opens>Enter a name and for Location select East US 2> Click Review + Create (Not Shown)> Click Create.
Figure below shows Resource Group HKTest Dashboard. Currently there are no resources to display as it is a new created group.
Note : Azure Policies is already discussed in Subscription Chapter. Policies can be applied at Subscription or Resource Group Level.
Azure Policy helps in implementing IT Governance in an organisation. IT Governance ensures that your organization is able to achieve its goals through an effective and efficient use of IT. IT Governance involves planning and initiative at strategic level to prevent IT issues from derailing IT projects.
Azure Policy is a managed service in Azure that is used to assign and manage policies. These policies enforce rules so that resources stay compliant with your corporate standards and service level agreements.
Azure Policy can be applied at Subscription, Resource Group or at Management Group level. Policy assignments are inherited by all child resources. However, you can exclude a subscope from the policy assignment.
There are Hundred built in Policies. Some of the built in policies include:
Allowed Storage Account SKUs : This policy definition has a set of conditions/rules that determine if a storage account that is being deployed is within a set of SKU sizes. Its effect is to deny all storage accounts that do not adhere to the set of defined SKU sizes.
Allowed Resource Type : This policy definition has a set of conditions/rules to specify the resource types that your organization can deploy. Its effect is to deny all resources that are not part of this defined list.
Allowed Locations : This policy enables you to restrict the locations that your organization can specify when deploying resources. Its effect is used to enforce your geo-compliance requirements.
In this Exercise we will assign Policy to Resource Group HKTest. This Policy allows creation of Storage Account with RA GRS replication option only.
Go to Resource Group HKTest Dashboard>Click Policies in left pane>Policies Blade open>Click Compliance in left pane.
Click Assign Policy in right pane>Assign Policy Blade opens as shown below.
Under Policy Defination click ellipsis … Box >Available Defination Blade opens>Scroll down to Allowed storage accounts SKU s.
Select Allowed storage accounts SKU s >Click Select (Not shown)> A drop down Box is created in Azure Policy Blade to select the required SKU> Here I selected Standard_RAGRS>Click Assign in Bottom of the pane (Not shown).
Policies dashboard shows the Policy created. It takes 15-20 minutes for Policy to take effect. You need to refresh it continuously.
In Azure Portal click create a Resource>Storage> Storage Account>Create Storage Account Blade opens>Select Resource Group HKTest> Enter a name> Select Location East US 2 > Make sure Replication is LRS .
Click Review +Create (Not shown) in above screen>Validation fails because of Policy. Our Policy only allowed RA-GRS where as we were creating Storage Account with LRS Replication.
You can move Azure VM to either a new subscription or a new resource group in the same subscription.
When moving resources, both the source group and the target group are locked during the operation. Write and delete operations are blocked on the resource groups until the move completes.
You can't change the location of the resource. Moving a resource only moves it to a new resource group. The new resource group may have a different location, but that doesn't change the location of the resource.
Requirement for moving resources
You can move virtual machines with the managed disks, managed images, managed snapshots, and availability sets with virtual machines that use managed disks. Managed Disks in Availability Zones can't be moved to a different subscription.
Virtual Machines with certificate stored in Key Vault can be moved to a new resource group in the same subscription, but not across subscriptions.
Virtual Machine Scale Sets with Standard SKU Load Balancer or Standard SKU Public IP can't be moved.
Virtual machines created from Marketplace resources with plans attached can't be moved across resource groups or subscriptions. Deprovision the virtual machine in the current subscription, and deploy again in the new subscription.
In this exercise we will move Public IP DPIPCloud in Resource Group RGCloud to Resource Group HKTest. Public IP DPIPCloud was created Exercise 9, Chapter 1. Similarly you can move VMs.
To move resources go to the resource group with those resources, and then select the Move button.
Go to Resource Group RGCloud Dashboard>In Right pane Click Move> When You Click Move Button you get 2 options- Move to another Resource Group or Move to another Subscription.
When You Click Move Button you get 2 options- Resource Groups or Subscription>Click Move to another Resource Group>Scroll down and Select Public IP DPIPCloud >Select Resource Group HKTest from dropdown box> Check Mark Terms & Conditions>Click OK.
Go to Resource Group HKTest Dashboard>You can see Public DPIPCloud has moved from Resource Group RGCloud to Resource Group HKTest.
You can tag resource or resource group with name/value pairs to categorize and view resources across resource groups and across subscriptions. Using tags you can logically organize Azure resources by categories.
Each tag consists of a name and a value.
Tags enable you to retrieve related resources from different resource groups. This approach is helpful when you need to organize resources for billing or management.
Each resource or resource group can have a maximum of 15 tag name/value pairs. If you want to associate more than 15 values with a resource, use a JSON string for the tag value.
Make sure that VMFE1 is running. In Azure Portal go to VM VMFE1 dashboard and click Tag in left pane>Add Tag opens in Right Pane> I entered Mktg in Name and VM in Value>Click Save.
Note: VM VMFE1 was created in Exercise 18, Chapter 2.
Go to VM VMFE1 Dashboard> In left pane Click Disks> In right pane Click VMFE1 OS Disk> OS Disk Pane opens>Click Tag in left pane>In Right pane in Name enter Mktg and Value Enter OS >Click Save
In Azure Portal go Cost Management dashboard>Click cost Analysis in left pane> In Right pane click Add filter >From Dropdown box select Tag>From Dropdown box select Mktg>From Dropdown box select os and vm> You can see total cost of VM VMFE1 and OS disk.
Locks are applied at subscription, resource group, or resource level to prevent users from accidentally deleting or modifying critical resources.
You can set the lock level to CanNotDelete or ReadOnly.
CanNotDelete means authorized users can still read and modify a resource, but they can't delete the resource.
ReadOnly means authorized users can read a resource, but they can't delete or update the resource.
When you apply a lock at a parent scope, all resources within that scope inherit the same lock.
Resource Manager Locks apply only to operations that happen in the management plane, which consists of operations sent to https://management.azure.com. The locks do not restrict how resources perform their own functions. Resource changes are restricted, but resource operations are not restricted.
For example a ReadOnly lock on a SQL Database prevents you from deleting or modifying the database but it does not prevent you from creating, updating or deleting data in the database. Data transactions are permitted because those operations are not sent to https://management.azure.com.
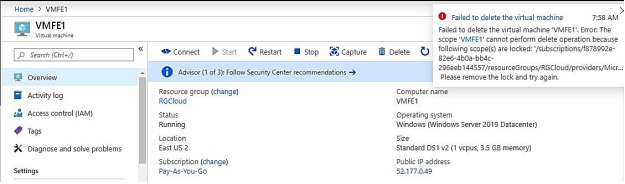
Go VMFE1 dashboard>Click Lock in left pane>In right pane Click + Add> Add Lock blade opens>Enter a name and from dropdown box select Delete and optionally add description about lock>Click OK.
In VMFE1 dashboard Click overview in left pane>In Right pane Click Delete> Delete VM Box pops up>Click Yes> You get notification Failed to Delete the Virtual Machine.

Top Training Courses










LIMITED OFFER: GET 30% Discount
This is ONE TIME OFFER

A confirmation link will be sent to this email address to verify your login. *We value your privacy. We will not rent or sell your email address.
Download Free Demo of VCE Exam Simulator
Experience Avanset VCE Exam Simulator for yourself.
Simply submit your e-mail address below to get started with our interactive software demo of your free trial.