- Home
- SY0-501 Section 2.2 – Summarize the security implications of integrating systems and data with third parties
SY0-501 Section 2.2 – Summarize the security implications of integrating systems and data with third parties
On-boarding/off-boarding business partners
Transitioning with a business partner occurs either during the on-boarding or off-boarding of a business partner. Both the initialization and the termination of a close business relationship have serious security issues.
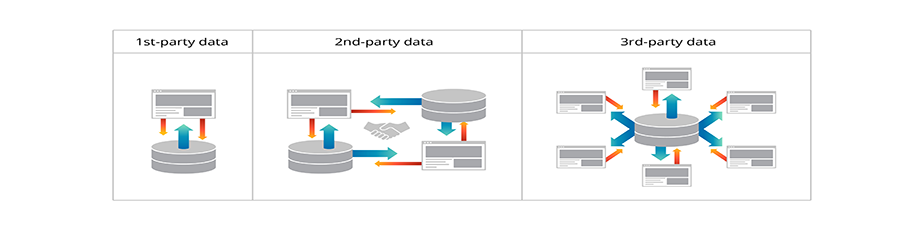
During the on boarding of a new business partner, it is important to determine whether the security policies of both organizations are compatible, at least in areas where the two companies’ networks will interact. One area that usually does get adequate attention from most companies is the issue of interoperability agreements. These are documents that define how the two organizations’ systems will interoperate and what the minimum requirements and expectations are. Just as important is the issue of who owns the data and how that data will be backed up. In a joint enterprise, data may be combined from both organizations. It must be determined, in advance, who is responsible for that data and how the data backups will be managed.
Data backup issues include how frequently to back up, how and where to store backup media, and how to test the backup media.
It is also critical to consider privacy considerations. Certain businesses, such as medicalrelated companies, have specific, legally mandated privacy requirements. However, any business that has any personal data must take into consideration the security of that data. When two different organizations are interoperating, ensuring that both organizations maintain a minimum level of privacy protection is important.
Social media networks and/or applications
Many companies allow full use of social media in the workplace, believing that the marketing opportunities it holds outweigh any loss in productivity. What they are unknowingly minimizing are the threats that exist. Rather than being all new threats, the social networking/media threats tend to fall in the categories of the same old tricks used elsewhere but in a new format. A tweet can be sent with a shortened URL so that it does not exceed the 140-character limit set by Twitter; unfortunately, the user has no idea what the shortened URL leads to—it could be to a phishing site, a downloadable Trojan, or just about anything else.
Interoperability agreements
There are some specific documents that need to be part of any interoperability agreement. Those are described here:
SLA: The Service-Level Agreement The SLA defines the level of service to be provided. For example, with a company providing technical support, the SLA will determine the response time (for example, will a tech be on site within 4 hours? 8 hours?) and the level of response (will there be a replacement part if needed?).
BPO: The Blanket Purchase Order This is usually applicable to government agencies. It is an agreement between a government agency and a private company for ongoing purchases of goods or services.
MOU: The Memorandum of Understanding This document is used in many settings in the information industry. It is a brief summary of which party is responsible for what portion of the work. For example, Company A may be responsible for maintaining the database server and Company B may be responsible for telecommunications.
ISA: The Interconnection Security Agreement This is an agreement between two organizations that have connected systems. The agreement documents the technical requirements of the connected systems.
All documented standards are subject to verification. The documents represent the standards that are agreed upon, but it is necessary to periodically verify compliance and performance standards. This can be done through a review of procedures, an actual audit, or even a vulnerability scan or penetration test. The level of review is up to the two parties involved.
Risk awareness Communication and awareness help ensure that security information is conveyed to the appropriate people in a timely manner. Most users aren’t aware of current security threats. If you set a process in place to explain concisely and clearly what is happening and what is being done to correct current threats, you’ll probably find the acceptance of your efforts to be much higher.
Communication methods that have proven to be effective for disseminating information include internal security websites, news servers, and emails. You might want to consider a regular notification process to convey information about security issues and changes.
In general, the more you communicate in a routine manner, the more likely people will internalize the fact that security is everybody’s responsibility.
Unauthorized data sharing
One of the major reasons to implement a cryptographic system is to ensure the confidentiality of the information being used. Confidentiality may be intended to prevent the unauthorized dis- closure of information in a local network or to prevent the unauthorized disclosure of information across a network. A cryptographic system must do this effectively in order to be of value.
The need to keep records secure from internal disclosure may be just as great as the need to keep records secure from outside attacks. The effectiveness of a cryptographic system in preventing unauthorized decryption is referred to as its strength: A strong cryptographic system is difficult to crack. Strength is also referred to as the algorithm’s work factor: The work factor describes an estimate of the amount of time and effort that would be needed to break a system.
The system may be considered weak if it allows weak keys, has defects in its design, or is easily decrypted. Many systems available today are more than adequate for business and personal use, but they are inadequate for sensitive military or governmental applications.
Cipher suites, for example, work with SSL/TLS to combine authentication, encryption, and message authentication. Most vendors allow you to set cipher suite preferences on a server to determine the level of strength required by client connections. With Sybase, for example, you set the cipher suite preference to Weak, Strong, FIPS, or All. If you choose Strong, you are limiting the choices to only encryption algorithms that use keys of 64 bits or more. Choosing Weak adds all the encryption algorithms that are less than 64 bits, while choosing FIPS requires encryptions, hash and key exchange algorithms to be FIPS- compliant (AES, 3DES, DES, and SHA1). Apache offers similar choices but instead of the words Strong and Weak, the names are changed to High, Medium, and Low.
Data ownership
Data ownership becomes an issue with BYOD. If the device is personally owned but used for company business, who owns the data on the device? The company or the individual? Related to that is the issue of support ownership. Is the individual responsible for support or the company? Patch management is closely related to support ownership. Who will be responsible for ensuring the personal device has patches updated? Antivirus management is another related issue. What antivirus software will be used? How will it be updated? These are all important questions that will need to be answered.
Adherence to corporate policies is an obvious issue. If individuals own their own devices, which they have purchased with their own funds, ensuring the user and the device adheres to corporate policies will be a challenge. Related to that issue is legal concerns. When a device is owned by the individual but used for company business, a number of legal issues arise. As just one example, what if the device is used to send spam? Is the company responsible? Another example would involve the employee leaving the company. How does the organization verify the device does not have any proprietary data on it? Forensics is another legal issue. If there is, for example, litigation against the company, usually computer records are subpoenaed, but the data that might reside on a personal device is a legal gray area.
Data backups
At the most basic level, fault tolerance for a server means a data backup. Backups are simply the periodic archiving of the data so that if there is a server failure you can retrieve the data. Although database administrators may use a number of different types of data back- ups (for example, transaction log backups), from a security point of view there are three primary backup types with which we are concerned:
Full All changes to the data are archived.
Differential All changes since the last full backup are archived.
Incremental All changes since the last backup of any type are archived.
So consider a scenario where you do a full backup at 2 a.m. each morning. You are concerned about the possibility of a server crash before the next full backup, so you want to do a backup every two hours. The type of backup you choose will determine the efficiency of doing those frequent backups and the time needed to restore data. Let’s consider each scenario and what would happen if the system crashes at 10:05 a.m.
Full Backup In this scenario, assume a full backup is done every two hours beginning at 2 a.m. When the system crashes at 10:05 a.m., you simply need to restore the 10:00 a.m. full backup. However, running a full backup every two hours is very time consuming and resource intensive, and it will have a significant negative impact on your server’s performance.
Differential Backup In this scenario, you do a full backup at 2 a.m. and then perform a differential every two hours thereafter. When the system crashes at 10:05 a.m., you have to restore the full backup from 2 a.m. and the differential backup from 10 a.m. This takes just one more step than restoring the full backup. Keep in mind, however, that the differential backups are going to get larger each time you do them and thus more time consuming and resource intensive. Although they won’t have the impact of the full backups, they will still slow down your network.
Incremental Backup In this scenario you do a full backup at 2 a.m. and then an incremental backup every two hours. When the system crashes at 10:05 a.m., you need to restore the last full backup done at 2 a.m. and then each incremental backup done since then—and they must be restored in order. This is much more complex to restore, but each incremental backup is small and does not take much time, nor do they consume many resources.
Follow security policy and procedures
An organization’s security management policies don’t exist in a vacuum. Regulatory and governmental agencies are key components of a security management policy. These agencies have made large improvements over the last several years to ensure the privacy of information; several laws have been passed to help ensure that information isn’t disclosed to unauthorized parties. As a security professional, you must stay current with these laws because you’re one of the primary agents to ensure compliance.












