- Home
- Uncategorized
Uncategorized
Top 5 Linux Certifications: Choose Your Best One!
Earning an IT certification is the way to go if you are planning on growing your career. For the tech professionals, the Linux credentials considered some of the best in the IT industry. That is why, in this blog article, we will take a look at the top five certificates that you might want to obtain before the end of this year. If earning such a credential is one of your goals for the nearest future, it is not late to pursue it. Let’s explore the best IT credentials that…

Top 7 Certifications for Your Time and Money
Getting the IT certificates is generally valuable. They boost your resume and your job potential. Of course, time, money, and effort that you put into obtaining these credentials differ from one to another. Interestingly, investing a lot in one certification doesn’t mean that another with less investment will not be important. The hard truth is that all of them are not the same and some give you a better perspective than others regardless of price or endeavor. Here, we take a look at some top certifications that are worth your…

Environments SCADA (supervisory control and data acquisition) refers to equipment often used to manage automated factory equipment, dams, power generators, and similar equipment. The Security+ exam does not heavily emphasize this, because the security measures will depend on the device. However, the infamous Stuxnet virus targeted specific SCADA equipment, so the need for SCADA security is not simply hypothetical. Embedded systems (such as printers, smart TVs, and HVAC controls) have their own security needs. Most modern printers, even midrange printers, have hard drives, RAM, and an operating system. That means…
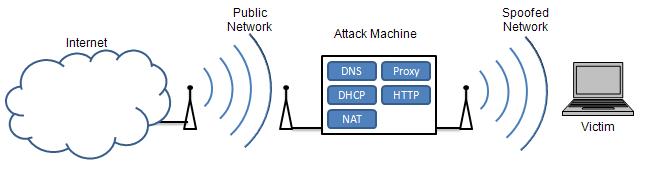
SY0-501 Section 3.4-Explain types of wireless attacks.
Wireless networking, more commonly termed as Wi-Fi, is the technology that opens your PDA or laptop computer to the world. However this technology is quite vulnerable to many exploits. A malicious intruder can use the most basic software to detect and capture the signal of your wireless device, along with usernames, passwords, emails and other data you would prefer to keep confidential. An intruder doesn’t have to be inside of your home or office building to manipulate a wireless signal. For example, they could be sitting outside in their car…

SY0-501 Section 2.9 given a scenario; select the appropriate control to meet the goals of security.
Confidentiality One of the major reasons to implement a cryptographic system is to ensure the confidentiality of the information being used. Confidentiality may be intended to prevent the unauthorized dis- closure of information in a local network or to prevent the unauthorized disclosure of information across a network. A cryptographic system must do this effectively in order to be of value. The need to keep records secure from internal disclosure may be just as great as the need to keep records secure from outside attacks. The effectiveness of a cryptographic…

SY0-501 Section 1.5 -Given a scenario, troubleshoot security issues related to wireless networking.
WPA WPA is Wi-Fi Protected Access, one of several popular standards for wireless network security. This WPA is not to be confused with Windows XP Product Activation, a separate technology that is also included with the Microsoft Windows operating system. Before being able to use Wi-Fi WPA with Windows XP, you may need to upgrade one or more components of your network including the XP operating system and network adapters on some computers as well as the wireless access point Follow these instructions to set up WPA on Wi-Fi networks…

SY0-501 Section 1.4 – Given a scenario, implement common protocols and services.
IPSec Internet Protocol security (IPsec) uses cryptographic security services to protect communications over Internet Protocol (IP) networks. IPsec supports network-level peer authentication, data origin authentication, data integrity, data confidentiality (encryption), and replay protection. The Microsoft implementation of IPsec is based on Internet Engineering Task Force (IETF) standards. In Windows 7, Windows Server 2008 R2, Windows Vista and Windows Server 2008, you can configure IPsec behavior by using the Windows Firewall with Advanced Security snapin. In earlier versions of Windows, IPsec was a stand-alone technology separate from Windows Firewall. One of…

As you’re searching for IT jobs with the rest of the population, it can be a bit nerve-wracking as you begin to question whether your resume, job experience, or CV is really sticking out like you want it to. You’ve probably been told time and time again that a good CV is a way to get that job that you want — but no one ever really tells you what that even means. What makes a CV a good CV? And how can you get there? Whether you’re a network…

5 Microsoft Certifications To Boost Your Career In IT
Microsoft delivers a prospect for IT pros to authenticate their experience through a multiplicity of renowned certification courses. With numerous choices available, a number of enthusiastic system technicians aren’t sure from where to take a start. The most efficacious information technology professionals can categorize Microsoft elucidations their companies actually require and are enthusiastic enough to train in order to fill that title role. In spite of everything, no one desires to undertake a designation they actually dislike. If you are a system analyst or technician that is enthusiastic enough to…

Job Opportunities For MCSE Certification
Microsoft MCSE Certification validates your skills in designing, implementing and maintaining Windows Server 2000-2003 based foundations. Prior MCITP and MCTS certifications available; the MCSE certification was go-to credential for tech professionals specialized in implementing and maintaining Microsoft technologies. Microsoft MCSE certification package authenticates your proficiency in designing, executing and managing corporates infrastructures running Windows Server 2003 or Windows Server 2000. Becoming a Certified Systems Engineer demonstrates clients and employers that you can design, implement, and maintain infrastructures specifically based upon Windows Server platform. This involves installing, troubleshooting networks and using…



