- Home
- Blog
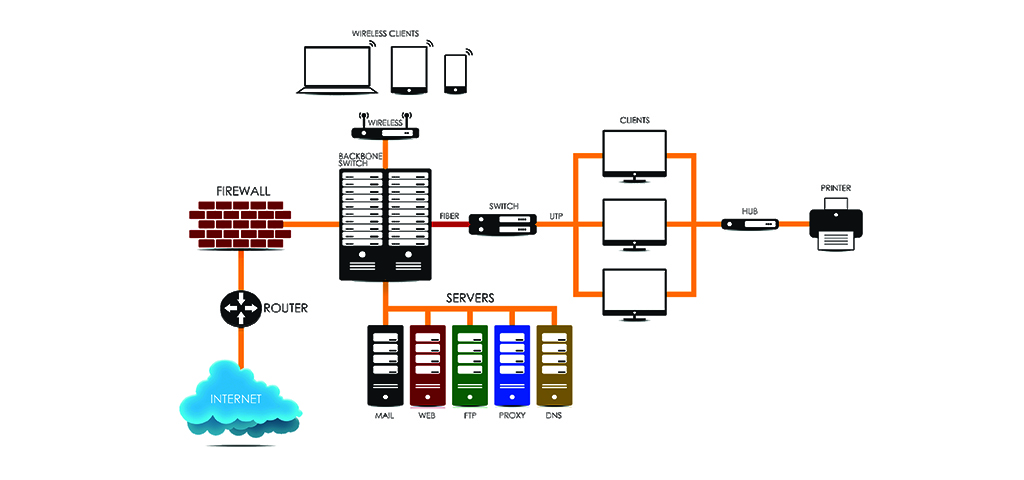
Essential Roles of a System Administrator in IT Infrastructure
In today’s technology-driven world, organizations rely heavily on their IT infrastructure to support daily operations, ensure communication, and maintain a competitive advantage. The backbone of this infrastructure is the system administration function, which is crucial for the seamless functioning of all hardware and software components. System administrators, often referred to as sysadmins, are the professionals responsible for managing these complex systems, ensuring their availability, performance, and security. This section introduces the concept of system administration, explains why it is essential, and provides an overview of the responsibilities that sysadmins typically…
The Ultimate Guide to Social Engineering: What You Should Know
Social engineering is a method of manipulating people into giving up confidential information or performing actions that compromise security. Unlike traditional hacking techniques that exploit vulnerabilities in software or hardware, social engineering targets the human element. It takes advantage of psychological weaknesses, trust, and natural tendencies to trick individuals into revealing sensitive data or allowing unauthorized access. In essence, social engineering relies on deception and persuasion rather than technical exploits. The attacker creates a scenario designed to appear legitimate and convincing, often impersonating a trusted person or institution. This can…
What Is Artificial Intelligence in Cybersecurity
Artificial Intelligence (AI) is a branch of computer science focused on creating systems capable of performing tasks that normally require human intelligence. These tasks include reasoning, learning, problem-solving, perception, and language understanding. In the realm of cybersecurity, AI refers to the application of these intelligent systems to protect digital infrastructures, detect cyber threats, and respond to attacks efficiently. Cybersecurity involves protecting computers, networks, programs, and data from unauthorized access, damage, or theft. Traditional cybersecurity systems often rely on predefined rules and signature-based detection methods, which are effective against known threats…
Key Applications and Real-World Use Cases in Cybersecurity
Cybersecurity has become one of the most critical aspects of modern digital life. As technology evolves and more systems connect to the internet, the risks and vulnerabilities also increase. Cyber attacks have grown more sophisticated, targeting everything from individual users to large corporations and government agencies. Consequently, cybersecurity applications and their practical use cases have expanded and diversified to meet these challenges. Understanding the key cybersecurity applications and how they are used in the real world is essential for anyone involved in IT, business, or digital safety. This part explores…
How to Become a Cybersecurity Analyst in 2025: A Step-by-Step Guide
Understanding the Educational Requirements The path to becoming a cybersecurity analyst typically starts with formal education. While not mandatory in all cases, most employers prefer candidates with at least a bachelor’s degree in computer science, information technology, cybersecurity, or a related field. In 2025, academic programs will have evolved to include courses tailored to modern cybersecurity challenges, such as cloud security, AI in cybersecurity, and cyber law. These programs provide students with foundational knowledge in networking, operating systems, and programming, which are crucial for understanding how systems function and how…
Exploring the Salary Landscape for Cybersecurity Jobs in Canada
The cybersecurity industry in Canada has witnessed significant growth over the past decade, driven by the rapid digital transformation of businesses and government agencies. As organizations increasingly rely on technology to manage data and conduct operations, the risk of cyber threats has risen dramatically. This has made cybersecurity a critical component for protecting sensitive information, infrastructure, and the privacy of individuals. The Canadian government and private sector recognize the importance of safeguarding digital assets, which has translated into growing investments in cybersecurity measures and workforce expansion. Canada’s cybersecurity landscape is…
Systems Engineer Role Explained: Everything You Should Know
A systems engineer is a professional responsible for designing, integrating, and managing complex systems over their entire life cycle. Unlike specialists who focus on specific components, systems engineers take a holistic approach, ensuring that all parts of a system work together efficiently and effectively. Their goal is to create systems that fulfill the required functions while meeting constraints such as cost, schedule, and quality. Systems engineering is an interdisciplinary field that involves working with hardware, software, processes, and people to deliver complete and functioning systems. This role often requires balancing…
Emerging Cybersecurity Trends You Can’t Ignore in 2025
As we move deeper into 2025, the cybersecurity landscape is becoming more complex and challenging than ever before. The rapid pace of technological innovation, combined with an increasingly connected world, has expanded the digital attack surface dramatically. Cyber threats are no longer limited to simple hacking attempts or isolated incidents; they now involve highly sophisticated campaigns orchestrated by well-funded criminal groups and nation-states. These actors exploit vulnerabilities in systems, software, and human behavior to cause significant harm ranging from data theft and financial fraud to infrastructure disruption and national security…
A Comprehensive Guide to the Six Types of Information Systems with Real-World Examples
An information system is a structured set of components and resources that collects, processes, stores, and distributes information to support decision-making, coordination, control, analysis, and visualization in an organization. It serves as the backbone for business operations and management by facilitating the flow of data and information across different levels and functions. Information systems combine people, processes, technology, and data to help organizations achieve their goals more efficiently and effectively. The integration of hardware, software, databases, telecommunications, and human resources enables businesses to manage vast amounts of information and respond…
Becoming a Cybersecurity Consultant: Pathway to Expertise and Career Advancement
In today’s fast-paced digital world, cybersecurity has become one of the most critical areas of concern for businesses, governments, and individuals alike. With the rise in cybercrime, data breaches, and security vulnerabilities, organizations are constantly seeking ways to protect their valuable digital assets. This is where cybersecurity consultants come into play. Cybersecurity consultants are experts who help organizations identify, assess, and address security risks within their digital infrastructures. Whether it’s evaluating existing security measures, designing new systems, or responding to a cyberattack, cybersecurity consultants play a crucial role in safeguarding…
Popular posts
Recent Posts
- In-Depth Analysis of Solution Architect Salaries in the UK
- AWS Redshift Explained: Key Benefits, Pricing Details, and Setup Steps
- Kickstart Your Cloud Architect Career in 2025: A Step-by-Step Guide
- Steps to Becoming a Certified Azure Architect
- Best AWS Solutions Architect Books: Your Complete Guide to Certification & Cloud Mastery