Use VCE Exam Simulator to open VCE files

Get 100% Latest Microsoft Certified: Azure Enterprise Data Analyst Associate Practice Tests Questions, Accurate & Verified Answers!
30 Days Free Updates, Instant Download!
Microsoft Certified: Azure Enterprise Data Analyst Associate Certification Practice Test Questions, Microsoft Certified: Azure Enterprise Data Analyst Associate Exam Dumps
ExamSnap provides Microsoft Certified: Azure Enterprise Data Analyst Associate Certification Practice Test Questions and Answers, Video Training Course, Study Guide and 100% Latest Exam Dumps to help you Pass. The Microsoft Certified: Azure Enterprise Data Analyst Associate Certification Exam Dumps & Practice Test Questions in the VCE format are verified by IT Trainers who have more than 15 year experience in their field. Additional materials include study guide and video training course designed by the ExamSnap experts. So if you want trusted Microsoft Certified: Azure Enterprise Data Analyst Associate Exam Dumps & Practice Test Questions, then you have come to the right place Read More.
Unpacking the Microsoft Azure Enterprise Data Analyst Exam
The world of data has become both vast and intricate, with enterprises depending heavily on analytics to steer decisions, identify opportunities, and manage risks. Within this data-driven environment, the role of a certified professional carries immense value. Among the distinguished credentials available today, the Microsoft Azure Enterprise Data Analyst Exam stands as a powerful measure of capability, proving that individuals can design, manage, and visualize complex analytical solutions at scale within Microsoft’s cloud ecosystem.
For those eager to solidify their standing in the analytics field, understanding the purpose and scope of this exam is fundamental. It represents more than a technical assessment—it is a recognition of one’s ability to transform raw information into meaningful intelligence and orchestrate data across enterprise environments.
Known formally as DP-500, the Microsoft Azure Enterprise Data Analyst Exam assesses expertise across several dimensions of large-scale analytics. It goes far beyond testing basic familiarity with tools; instead, it emphasizes the construction of resilient data models, the management of intricate repositories, and the capacity to convey insights through visualization. A professional undertaking this exam is expected to show fluency in technologies like Power BI and Azure Synapse Analytics while demonstrating mastery of essential languages and frameworks such as Transact-SQL, Power Query, and Data Analysis Expressions.
This exam is designed with enterprise demands in mind. Organizations often deal with massive data volumes that require not only efficient processing but also scalable solutions capable of adapting as needs evolve. Candidates who succeed in this certification establish themselves as individuals who can handle such enterprise challenges, bridging the technical gap between raw information and actionable decision-making.
The global reliance on analytics has grown exponentially, and with it, the expectations placed upon data analysts have intensified. Employers now seek professionals who can do more than interpret charts—they want experts who can manage the entire architecture of analytics systems. The Microsoft Azure Enterprise Data Analyst Exam ensures that certified individuals have cultivated the capacity to design these environments, harness Azure’s robust infrastructure, and implement practices that optimize both performance and insight.
This credential also offers tangible professional benefits. Holding the certification signals credibility to employers, often leading to enhanced career opportunities and improved earning potential. Beyond financial considerations, it provides analysts with confidence, helping them stand out in a competitive field where organizations prioritize skilled practitioners who understand how to leverage advanced technologies.
At the heart of the exam lies a multidimensional framework of knowledge areas. The candidate must demonstrate an ability to design and implement enterprise-scale solutions. This requires constructing sophisticated models that can answer complex queries, setting up repositories that maintain integrity and reliability, and deploying tools like Azure Synapse Analytics to handle large datasets effectively.
Equally important is the visualization aspect, where candidates must prove adept at crafting insightful Power BI dashboards. This involves translating raw numbers into meaningful patterns that business leaders can act upon swiftly. The exam also measures competence in query languages, particularly Transact-SQL, which is foundational for managing relational databases. Power Query and Data Analysis Expressions further extend these capabilities, enabling professionals to shape, cleanse, and calculate data with finesse.
Each of these domains is interwoven with the others, demanding that candidates adopt a holistic approach. Mastery of individual components is insufficient unless one can integrate them cohesively into enterprise solutions that are both functional and scalable.
Success in the exam requires a well-balanced preparation strategy that intertwines theoretical study with experiential practice. Microsoft Learn provides structured pathways that guide learners step by step through fundamental topics like modeling, visualization, and analytics implementation. However, preparation cannot remain abstract. Candidates should immerse themselves in practical projects, constructing models, managing repositories, and deploying visualization tools in real-world scenarios.
This hands-on exposure allows candidates to internalize knowledge at a deeper level, ensuring that they can apply concepts under pressure rather than simply recalling them. Real-world practice also mirrors the environment in which certified analysts will eventually operate, building resilience and adaptability that pure study alone cannot achieve.
One element of Microsoft certifications that often catches candidates off guard is the scheduled retirement of exams. The DP-500 exam, like others, has a defined lifespan. For those planning to achieve certification, it becomes vital to remain aware of these timelines. Failure to schedule preparation and examination in accordance with the retirement calendar can result in missed opportunities, forcing candidates to pivot toward alternative certifications unexpectedly.
Maintaining vigilance through resources like Microsoft Learn ensures that professionals stay informed, safeguarding their progress and allowing them to align their study plans with available certification windows.
Earning this certification grants more than a digital badge; it opens gateways to professional advancement and recognition. The Microsoft Certification badge becomes a visible testament to expertise, serving as a credential that can be displayed on resumes, professional profiles, and networking platforms. This not only signals competence to potential employers but also engenders trust among peers and clients.
For many professionals, the badge translates directly into increased career opportunities, promotions, and in numerous cases, higher salaries. It also grants access to communities of certified practitioners, fostering opportunities for collaboration, mentorship, and continuous learning. In effect, the certification strengthens both individual career trajectories and professional networks.
Although many candidates gravitate toward manuals, guides, and study materials, genuine readiness emerges only through immersion in real-world applications. Enterprise-scale analytics is inherently complex, and the scenarios presented in the exam reflect this reality. By engaging in case studies, building sample dashboards, and simulating large-scale data deployments, candidates fortify their understanding of how theory translates into practice.
Employers likewise place greater value on professionals who demonstrate practical acumen. A certified analyst who has tested their skills in simulated enterprise projects becomes an asset capable of handling unforeseen challenges with confidence. This readiness ensures that the certification remains not merely academic but deeply functional in professional contexts.
Attaining certification represents a milestone, but it is equally important to view it as the beginning of a continuous journey. With the pace of technological advancement, analysts must stay agile, renewing their certifications when necessary and remaining abreast of evolving tools and methodologies. The Microsoft ecosystem itself is dynamic, introducing updates that reshape the way data is managed, visualized, and deployed.
For certified professionals, the credential serves as a foundation from which to pursue further specialization. Some may choose to move deeper into data engineering, while others may pursue leadership roles, overseeing analytics teams and enterprise strategies. In all cases, the certification amplifies possibilities, creating new avenues for growth while affirming expertise in a field that continues to expand in relevance.
The Microsoft Azure Enterprise Data Analyst certification holds a central place for those aiming to establish authority in the field of cloud-driven analytics. It is not merely a test of knowledge but a comprehensive evaluation of practical dexterity, strategic reasoning, and the capacity to harness advanced technologies for enterprise-scale analytics. The certification stands as a validation of one’s proficiency in manipulating large datasets, curating visualizations, and structuring data repositories with an architect’s precision.
Microsoft designed this recognition to align with the evolving dynamics of data management in modern organizations. Businesses today rely on seamless data flows and powerful insights derived from robust analytics platforms. Candidates preparing for this certification are expected to master not only the theoretical landscape but also the tangible implementation of solutions in real-world environments. With the growing emphasis on intelligent decision-making, Azure Synapse Analytics and Power BI form the foundation of what this credential demands.
The path toward becoming an Azure-certified data analyst requires fluency across several intertwined domains. First, it emphasizes a profound understanding of enterprise-scale repositories, where structured and unstructured data converge. Candidates must prove their competence in managing these repositories efficiently, ensuring accessibility while maintaining performance and governance.
Equally important is the ability to design models that transform raw data into coherent structures. Here, mastery of Data Analysis Expressions and Power Query plays a vital role, as they allow analysts to bring refinement and depth into analytics. The creation of dashboards and visualization reports, primarily through Power BI, demonstrates how technical ability translates into business-oriented storytelling.
Another cornerstone is the adept application of T-SQL for querying and data processing. This technical skill ensures that candidates can manipulate relational databases at scale, enabling complex transformations and seamless integration with broader enterprise solutions. Beyond the syntax, it tests the candidate’s intuition in crafting solutions that serve diverse organizational needs.
Preparation for this certification is significantly enriched by Microsoft Learn, a platform structured to provide modular learning paths and interactive exercises. By engaging with its resources, candidates can navigate through intricate domains such as data modeling, visualization techniques, and advanced analytics implementation. While the material provides theoretical understanding, its hands-on laboratories allow for the cultivation of real-world expertise.
Microsoft Learn emphasizes iterative practice, meaning learners can return repeatedly to strengthen areas where comprehension may initially falter. It creates a balance between structured academic-style instruction and experiential problem-solving, ensuring candidates are not limited to rote memorization but gain applicable insights.
The Microsoft Azure ecosystem is interconnected, and the DP-500 exam does not exist in isolation. Related credentials, such as PL-300, further complement the competencies tested here. While DP-500 hones in on enterprise-scale analytics, PL-300 reinforces skills in data modeling and advanced DAX applications. Analysts who aim for continuous growth often pursue both, creating a well-rounded profile that aligns with diverse organizational requirements.
The synergy between these certifications also demonstrates the layered structure of Microsoft’s professional recognition framework. Each credential builds on the other, with skills interwoven in such a way that professionals emerge with holistic expertise rather than isolated technical knowledge. This progression not only improves marketability but also encourages continuous learning and renewal.
Earning the Azure Enterprise Data Analyst certification translates into tangible professional benefits. Organizations place immense value on professionals capable of turning torrents of data into actionable intelligence. By achieving this recognition, analysts establish themselves as authorities capable of bridging technical complexity with business clarity.
Career advancement opportunities often expand considerably, as certified analysts are trusted to lead initiatives involving cloud-based repositories, interactive dashboards, and large-scale analytical models. Salary growth typically follows, with organizations willing to invest in professionals who bring validated expertise. Furthermore, certification opens doors to specialized communities, networking opportunities, and advanced learning resources available exclusively to credential holders.
Beyond monetary incentives, there is also a sense of professional elevation. Holding the badge of recognition not only signifies technical competence but also a commitment to the discipline of analytics as a vocation. It reflects resilience, dedication, and the capacity to adapt in a field where tools, methodologies, and business demands evolve ceaselessly.
Another dimension of the certification involves its renewal, ensuring professionals remain aligned with the latest advancements in the Azure ecosystem. Renewal cycles are typically every two years, with online assessments designed to evaluate continuing proficiency. These assessments are streamlined compared to initial examinations but require candidates to stay current with new features, updates, and industry trends.
The requirement for renewal is not merely a formality; it is an essential component of maintaining credibility. Organizations seek assurance that their analysts are equipped not only with past knowledge but also with an awareness of present and forthcoming innovations. By embracing the renewal cycle, professionals maintain relevance and safeguard their career trajectories against obsolescence.
The Azure Enterprise Data Analyst certification focuses heavily on practical application in cloud environments. A central feature is the ability to deploy and optimize Azure Synapse Analytics. This involves not only technical setup but also nuanced considerations such as scalability, cost management, and integration with other enterprise systems.
Proficiency in Power BI forms another major axis, with candidates expected to move beyond surface-level usage into sophisticated modeling, reporting, and interactive dashboard creation. These visualizations transform data into narratives that influence executive decisions and guide organizational strategies.
The application of T-SQL provides the backbone of querying and processing, reinforcing the analyst’s role as someone deeply embedded in the mechanics of relational databases. Combined with Power Query and DAX, it ensures professionals can handle the full spectrum of tasks, from raw ingestion to refined presentation.
Microsoft Azure has established itself as a linchpin for modern enterprise analytics. Its scalability, integration capabilities, and broad suite of tools empower organizations to harness data more effectively than ever before. Within this ecosystem, Synapse Analytics serves as a hub for large-scale processing, while Power BI provides the front-facing interpretative framework.
The Azure Enterprise Data Analyst certification validates the candidate’s ability to navigate this ecosystem holistically. Rather than viewing tools in isolation, certified professionals are trained to understand their interrelationships. This holistic grasp enables the construction of seamless pipelines where raw data flows into repositories, undergoes transformations, and emerges as actionable insights.
Power BI stands at the heart of the certification, reflecting its status as one of the most versatile tools in the analytics sphere. Its ability to connect with repositories, relational databases, and cloud services makes it indispensable for data analysts.
Certified professionals are expected to demonstrate dexterity in using Power BI for data modeling, generating real-time dashboards, and integrating with Azure Synapse for deeper insights. The tool’s compatibility with Power Query and DAX further enhances its scope, allowing analysts to create solutions that are not only visually compelling but also technically robust.
The importance of Power BI extends beyond technical function; it is also a storytelling instrument. Through its dashboards, professionals translate complex datasets into visual languages that resonate with decision-makers. This capacity to bridge raw numbers with human comprehension makes it one of the most prized skills in analytics.
The journey toward certification should not be confined to theoretical preparation. Candidates gain the most value when they immerse themselves in hands-on scenarios. This involves creating and managing repositories, experimenting with T-SQL queries, designing visualizations in Power BI, and simulating enterprise-scale deployments in Synapse Analytics.
Such practical immersion deepens comprehension and cultivates confidence. It allows candidates to confront unforeseen challenges and sharpen problem-solving instincts. By bridging theory with practice, professionals prepare themselves for both the exam and the day-to-day realities of working in a data-driven organization.
The journey to becoming a Microsoft Certified Azure Data Analyst Associate requires a profound grasp of the capabilities outlined in the DP-500 exam. This evaluation is more than a theoretical checkpoint; it measures one’s practical dexterity in designing and implementing enterprise-scale analytics solutions within Microsoft Azure. Candidates are expected to demonstrate command over a vast technical landscape, where data modeling, repository management, and advanced visualization techniques intersect with powerful cloud-based services such as Azure Synapse Analytics and Power BI. Preparing for this endeavor is a rigorous exercise in unifying conceptual knowledge with real-world application, ensuring that professionals are not only able to pass the exam but also deliver tangible value within complex organizational ecosystems.
One of the principal areas of the DP-500 exam is the ability to design analytics solutions that meet the intricate needs of modern enterprises. At its foundation, this requires familiarity with constructing and refining data models, ensuring they align with organizational objectives while remaining efficient and scalable. A data analyst must be capable of translating disparate datasets into coherent models that empower decision-making and allow for deeper exploration of business patterns.
Alongside modeling, repository management plays a pivotal role. Professionals are tested on their ability to organize and oversee repositories within Azure Synapse Analytics, ensuring that storage solutions are not only structured but also optimized for performance. This involves a nuanced understanding of partitioning, indexing, and query performance optimization, requiring candidates to balance technical precision with business imperatives.
Another indispensable aspect of this skill domain is the creation of effective visualizations. Using Power BI, analysts must transform raw figures into meaningful dashboards that provide clarity for stakeholders at every level of an organization. Visual storytelling becomes central here, as charts and reports must communicate trends, anomalies, and insights in ways that resonate beyond technical audiences.
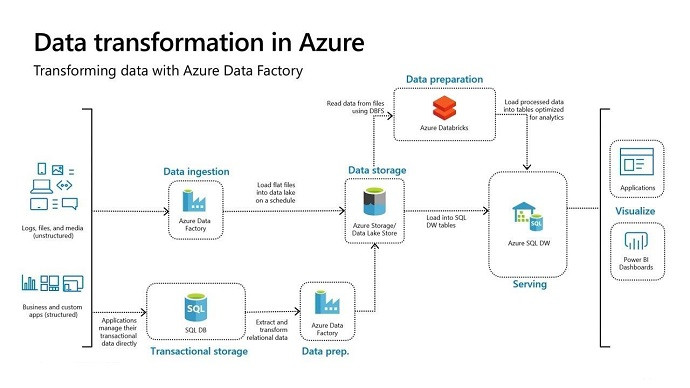
Azure Synapse Analytics lies at the heart of enterprise-scale data operations, and mastery of this platform is crucial for success in the DP-500 exam. Candidates are assessed on their ability to build pipelines that manage the flow of data from ingestion to transformation and delivery. This requires a detailed awareness of data integration methods, performance tuning strategies, and resource allocation, ensuring that large volumes of information can be processed seamlessly.
In addition, exam takers must be prepared to demonstrate fluency in deploying analytics solutions that integrate relational databases with advanced querying through T-SQL. The exam expects a professional to orchestrate data workflows that are secure, resilient, and capable of handling diverse business scenarios. This involves configuring workspaces, managing access controls, and deploying scalable workloads that cater to fluctuating business demands.
The use of Power BI extends far beyond the construction of simple reports. Within the scope of the DP-500 exam, candidates must show mastery in building interactive dashboards that respond dynamically to user queries and provide detailed insights into organizational operations.
Power BI requires the skillful integration of Data Analysis Expressions (DAX), enabling analysts to define calculations, measures, and aggregations that reflect complex business logics. The exam measures a candidate’s ability to design and deploy models that integrate DAX with relational structures, ensuring that insights are both accurate and adaptable.
Another important skill involves the application of Power Query. By cleansing, shaping, and transforming datasets, professionals can prepare information for analysis in ways that make visualizations more precise and meaningful. A candidate must show not only technical proficiency in using Power Query but also an understanding of when and how to apply its transformations in enterprise scenarios.
T-SQL is a cornerstone of the skills measured in DP-500, representing the technical foundation for managing relational databases within Azure environments. Candidates must show their proficiency in writing queries that extract, manipulate, and aggregate data at scale.
This requires competence in designing statements that join multiple tables, filter datasets, and perform calculations across vast repositories. Beyond basic queries, the exam challenges professionals to optimize their SQL logic for performance, particularly when dealing with massive volumes of enterprise data.
Transact-SQL also underpins the ability to ensure data integrity. Through functions, constraints, and validation mechanisms, analysts must maintain reliable structures that preserve accuracy and consistency. The combination of these skills enables professionals to support analytics workflows that are both robust and adaptable.
Data Analysis Expressions bring a layer of sophistication to analytics solutions, allowing for the creation of complex measures that extend far beyond basic aggregations. Within the DP-500 exam, professionals must demonstrate fluency in applying DAX to scenarios involving time intelligence, advanced filtering, and dynamic calculations.
When integrated into Power BI, DAX becomes an essential tool for providing stakeholders with tailored insights. Whether designing cumulative totals, calculating year-over-year comparisons, or building dynamic ranking models, a candidate must show both technical precision and creativity in applying DAX to real-world problems.
Advanced modeling skills are also emphasized. This involves developing star schemas, snowflake models, and composite structures that organize data efficiently while supporting scalable analytics. A well-architected model serves as the backbone of visualization efforts, ensuring that reports are both performant and intuitive.
Managing repositories effectively is one of the most practical skills evaluated in DP-500. Analysts must organize data storage solutions in ways that support rapid access and scalable growth. This involves familiarity with partition strategies, indexing methods, and data distribution techniques that optimize query performance.
Relational databases remain integral within enterprise ecosystems, and the exam evaluates candidates on their ability to integrate these structures with cloud-based repositories. Professionals must manage schemas, enforce relationships, and ensure that data is available for seamless visualization in Power BI.
These management tasks require a balance between technical mastery and organizational foresight, as analysts must not only maintain efficient repositories but also ensure compliance with security policies and governance frameworks.
The DP-500 exam emphasizes the ability to construct analytics solutions that span the entire lifecycle of data, from ingestion to visualization. Candidates must show competence in designing pipelines that draw from multiple sources, transform data into coherent structures, and present the results in accessible formats.
This holistic perspective requires a multidisciplinary skill set. Professionals must blend their expertise in Power Query, T-SQL, and Azure Synapse Analytics to construct pipelines that are both reliable and efficient. They must also consider cost optimization and resource management, ensuring that analytics operations remain sustainable in the long term.
End-to-end pipelines also demand attention to data governance. Exam candidates are expected to understand and apply principles of data security, privacy, and compliance, safeguarding sensitive information while enabling effective analysis.
To succeed in demonstrating these skills, candidates must take a disciplined approach to preparation. The most effective method involves combining structured learning paths on Microsoft Learn with hands-on experimentation in Azure environments. Practicing data modeling, repository management, and visualization under realistic conditions ensures that knowledge becomes deeply ingrained.
Practice assessments can further reinforce readiness by identifying areas of weakness and offering targeted remediation. By simulating exam conditions, candidates can develop the resilience and confidence necessary to navigate the exam with composure.
Staying informed about retirement dates and renewal requirements is equally important, as Microsoft certifications follow a structured timeline. Planning ahead ensures that candidates maximize the value of their certifications and remain aligned with evolving technologies.
Mastering the skills measured in DP-500 extends far beyond passing an exam. These competencies prepare professionals to become pivotal contributors within their organizations, capable of shaping analytics strategies that drive growth and innovation.
By demonstrating mastery in Synapse Analytics, Power BI, T-SQL, and DAX, certified analysts establish themselves as technical leaders in a competitive field. Their expertise not only validates their capacity to manage enterprise-scale data but also positions them as visionaries who can unlock new opportunities through intelligent analytics.
Secure Shell has transcended its original purpose of remote logins to become an indispensable cornerstone of contemporary network security. Organizations today rely on it not only for managing servers but also for ensuring cryptographic integrity across vast and diverse digital ecosystems. SSH underpins countless automated tasks, from routine software updates to orchestrated system administration. With enterprises migrating to hybrid environments, its capacity for safeguarding communication channels is paramount. In this sense, SSH operates as a silent guardian, preserving the confidentiality of transmissions even in highly volatile digital landscapes.
Its versatility makes it suitable for organizations of all sizes. For smaller businesses, SSH provides a straightforward mechanism to protect sensitive exchanges without requiring excessive investment in additional infrastructure. For global enterprises, SSH keys and tunnels facilitate continuous workflows by enabling secure cross-border collaboration. With cyber adversaries employing increasingly sophisticated tactics, maintaining secure channels for administrative and operational activity is indispensable.
The proliferation of cloud computing has intensified the demand for robust security measures. Public, private, and hybrid clouds rely heavily on SSH to secure the vast array of servers and services that underpin their operations. Engineers can use SSH keys to manage cloud-based virtual machines without compromising credentials. It offers the added advantage of scalability, since automated systems can be configured to authenticate securely across thousands of nodes.
Cloud orchestration tools frequently embed SSH into their processes, whether they are provisioning new instances or deploying applications across multiple regions. SSH tunnels can be used to connect isolated cloud environments securely, ensuring sensitive workloads remain shielded from potential intrusion. As cloud-native applications grow increasingly complex, the role of SSH in maintaining the confidentiality and integrity of these workloads has never been more pivotal.
One of SSH’s most transformative uses is its integration into automated workflows. System administrators and DevOps practitioners harness SSH to execute scripts across fleets of machines, drastically reducing the time and effort required for repetitive tasks. For example, software patches, system monitoring, and log collection can all be automated securely through SSH connections.
The concept of Infrastructure as Code, where servers and applications are configured programmatically, owes much of its feasibility to SSH. By providing a secure channel for commands and data, SSH ensures that automation does not sacrifice confidentiality. Furthermore, its flexibility allows integration into orchestration platforms, where hundreds of machines must be managed with precision. This symbiotic relationship between automation and SSH accelerates deployment cycles while maintaining security standards.
The rise of DevOps practices has underscored the importance of secure, automated communication between development and operations teams. SSH plays a vital role in this ecosystem by enabling continuous integration and deployment pipelines. Whenever developers push new code to repositories, SSH is often used to authenticate and transmit updates to build servers or staging environments.
This seamless interaction is essential in environments where software changes occur frequently. By embedding SSH into the pipeline, organizations ensure their deployments remain tamper-proof while enabling rapid innovation. Its cryptographic underpinnings also support the trust model necessary for distributed teams, ensuring that only authorized entities can alter critical systems.
The Internet of Things has introduced billions of interconnected devices, many of which require secure management. SSH is increasingly being adopted in this realm to facilitate remote access, firmware updates, and monitoring of devices. Without such secure channels, IoT ecosystems would be vulnerable to interception and manipulation.
Given the resource constraints of many IoT devices, lightweight implementations of SSH are being developed to strike a balance between security and efficiency. Manufacturers are recognizing the necessity of embedding such capabilities from the outset, as retrofitting devices with security mechanisms often proves impractical. SSH ensures that data traveling between sensors, gateways, and servers cannot be intercepted by malicious actors.
While SSH provides robust security, the widespread use of SSH keys introduces its own challenges. Organizations managing thousands of servers often grapple with key sprawl, where credentials proliferate without adequate oversight. Without proper governance, expired or unused keys can pose serious security risks, potentially allowing unauthorized access.
Best practices involve implementing centralized management tools that track, rotate, and retire keys systematically. By enforcing stringent policies and automating key lifecycle management, enterprises can mitigate the risks associated with credential mismanagement. Auditing mechanisms also help organizations maintain visibility, ensuring compliance with industry regulations while minimizing exposure to internal or external threats.
Many industries operate under strict compliance mandates requiring demonstrable measures to secure sensitive data. SSH aligns with these demands by providing encrypted channels that safeguard against interception. Financial institutions, healthcare providers, and governmental organizations all rely heavily on SSH to remain compliant with regulatory frameworks.
Auditing capabilities associated with SSH sessions enhance accountability by documenting who accessed which resources and when. This traceability is vital in industries where transparency and evidence of secure practices are mandatory. By embedding SSH into their compliance strategies, organizations ensure that their security protocols withstand scrutiny during audits.
As quantum computing advances, traditional cryptographic algorithms face potential obsolescence. Researchers are already investigating post-quantum cryptographic methods to ensure SSH remains resilient in the decades ahead. The cryptographic backbone of SSH will likely evolve to incorporate quantum-resistant algorithms, maintaining its relevance in an era of transformative computation.
Forward-looking organizations are already monitoring developments in this field, preparing for gradual transitions as standards emerge. This proactive stance ensures that SSH remains a future-proof solution, capable of protecting communications even against quantum-enabled adversaries.
Cybersecurity strategies increasingly incorporate SSH not only for administration but also as part of active defense mechanisms. Security teams leverage SSH tunnels to investigate compromised systems without exposing themselves to further risk. By connecting securely to quarantined environments, analysts can dissect malware, identify vulnerabilities, and implement remediation with reduced danger.
Additionally, SSH’s integrity verification supports secure patching practices. During widespread vulnerabilities, organizations must deploy updates rapidly without compromising trust. SSH ensures these updates are delivered securely, forming an indispensable tool in the arsenal of modern cyber defense.
The global shift toward remote work has elevated the importance of secure communication tools. SSH provides employees and administrators alike with a mechanism to connect securely to corporate resources from diverse locations. Its authentication mechanisms, particularly when using key pairs, reduce reliance on vulnerable password-based systems.
In a distributed workforce, maintaining operational continuity while preserving security is paramount. SSH bridges this divide, enabling productivity without conceding security. From remote server management to secure file transfer, its versatility aligns seamlessly with the needs of geographically dispersed teams.
Academic and research institutions, often operating with limited resources but handling sensitive data, depend heavily on SSH. Scholars and scientists use SSH to access shared supercomputers, transfer large datasets, and collaborate across borders. The encrypted channels ensure that intellectual property and confidential research remain secure from prying entities.
Furthermore, the collaborative ethos of academia aligns with SSH’s decentralized yet secure architecture. By providing a trustworthy medium for international cooperation, SSH enhances the pace of scientific progress while ensuring sensitive data does not fall into the wrong hands.
Beyond its technical applications, SSH reflects broader cultural and ethical considerations in the digital realm. It embodies the principle that privacy and confidentiality are not luxuries but fundamental rights in modern communication. By empowering individuals and organizations to shield their data, SSH plays a role in sustaining digital sovereignty.
Ethically, its deployment speaks to a commitment to transparency and accountability, ensuring that users can interact securely without unwarranted surveillance. In an era where digital ethics is gaining prominence, SSH’s role transcends technology, becoming an emblem of digital dignity.
Looking ahead, the trajectory of SSH is intertwined with the broader evolution of digital infrastructure. Its adaptability positions it as a mainstay even as new paradigms such as edge computing and 5G networks redefine connectivity. The increasing demand for secure automation, remote access, and compliance will only magnify its relevance.
By embracing ongoing innovations such as quantum-resistant encryption, centralized key management, and integration into emerging technologies, SSH will continue to thrive as a bulwark against cyber threats. Its enduring significance lies not only in its technical prowess but in its alignment with the timeless human need for trust and confidentiality.
In the digital age, organizations are constantly exposed to a wide array of dangers that evolve with time. Intrusion detection systems have become a core element in maintaining the security posture of businesses, government institutions, and even personal environments. These systems function as vigilant watchers, scrutinizing traffic and activities to identify patterns that may indicate malicious intent. Their role extends beyond traditional monitoring, as they now contribute to predicting attacks, understanding behavioral anomalies, and supporting compliance efforts across industries.
The dependence on digital platforms for commerce, communication, and administration has amplified the necessity of having strong mechanisms to detect intrusions. Without such safeguards, attackers could infiltrate networks, exfiltrate confidential data, and cripple essential services. Intrusion detection systems not only provide alerts in real time but also act as a protective layer against sophisticated schemes such as ransomware, denial-of-service attempts, and insider threats. Their indispensable nature lies in their capacity to reduce blind spots that conventional firewalls or antivirus tools might overlook.
Over the years, intrusion detection solutions have diversified into multiple forms, each with unique functions. Network-based systems analyze packets traversing a network to uncover irregularities, while host-based systems monitor activity within individual machines. There are also hybrid models that integrate both approaches to offer comprehensive visibility. The maturation of technology has led to further specialization, with anomaly-based detection focusing on unusual behavior and signature-based detection recognizing known attack patterns. This multi-pronged evolution reflects the dynamic landscape of digital adversities.
One of the most significant advancements in intrusion detection has been the adoption of artificial intelligence and machine learning. By training algorithms on vast amounts of traffic data, systems can identify subtle deviations that humans might miss. This augmentation not only enhances the speed of detection but also reduces the occurrence of false positives. The self-improving nature of machine learning models enables intrusion detection systems to adapt continually, thereby maintaining their effectiveness against attackers who regularly alter their tactics.
Intrusion detection systems rarely operate in isolation. They are frequently incorporated into larger ecosystems that include firewalls, endpoint protection platforms, and security information management tools. This integration allows for faster response, as alerts generated by detection systems can be correlated with data from other sources. The outcome is a holistic view of an organization’s security landscape, enabling incident response teams to act swiftly with contextual insights. Such synergy transforms isolated alerts into actionable intelligence, minimizing the time attackers can linger unnoticed within a network.
While intrusion detection systems are powerful, their deployment is not devoid of challenges. High network traffic volumes can overwhelm systems, leading to missed detections or increased latency. False positives remain another hurdle, as excessive alerts can desensitize security personnel, leading to overlooked incidents. Moreover, implementing detection systems requires meticulous configuration and continuous updates to remain aligned with emerging attack strategies. Addressing these challenges demands careful planning, sufficient resources, and skilled professionals capable of fine-tuning the systems for optimal outcomes.
Many industries operate under stringent data protection and security regulations, making intrusion detection systems vital for compliance. Organizations in healthcare, finance, and government are often required to demonstrate the ability to monitor and report on suspicious activities. By generating detailed logs and comprehensive reports, detection systems facilitate compliance audits and legal accountability. Their contribution is not limited to defense but extends to proving that organizations uphold security commitments mandated by law or industry standards.
Not all threats originate from external actors. Insiders with legitimate access may abuse privileges to compromise systems or steal valuable data. Intrusion detection systems are uniquely positioned to uncover such behavior by analyzing anomalies in user activities. For example, an employee downloading unusually large volumes of sensitive information may trigger an alert. This protective measure ensures that organizations are not solely focused on external breaches but are also attuned to risks that arise from within.
Despite the sophistication of technology, the human factor remains indispensable in intrusion detection. Analysts interpret alerts, investigate incidents, and decide on remediation strategies. Human expertise adds context that automated systems may not fully comprehend. Training, experience, and intuition empower analysts to discern between benign irregularities and genuine threats. The symbiotic relationship between technology and human oversight ensures that intrusion detection systems deliver their intended value effectively.
The trajectory of intrusion detection is poised to grow in tandem with technological innovation. As cloud computing, edge devices, and the Internet of Things proliferate, the complexity of monitoring will increase. Detection systems must evolve to cover dispersed and heterogeneous environments. Future advancements are likely to include deeper integration with artificial intelligence, enhanced automation of response measures, and greater adaptability to encrypted traffic analysis. The future vision is one of proactive defense, where systems not only detect but also anticipate and neutralize threats before they can inflict damage.
The exploration of intrusion detection systems across multiple perspectives reveals their indispensable role in sustaining the integrity of modern digital landscapes. They are not merely passive observers but active guardians that scrutinize, analyze, and respond to complex patterns of malicious activity. By examining their evolution, from network-based and host-based monitoring to anomaly detection and artificial intelligence–driven approaches, it becomes evident that these systems adapt constantly to outpace adversaries who refine their techniques with equal persistence. Their integration into broader security ecosystems transforms them into powerful instruments of collective defense, uniting alerts and insights into a coherent picture of organizational resilience. Beyond technical sophistication, they also embody accountability by supporting compliance with regulatory frameworks and reinforcing trust among stakeholders who demand secure stewardship of sensitive information. Challenges such as false positives, resource strain, and the need for continuous updates underscore that these systems are not standalone cures but integral parts of a wider security posture requiring expert oversight. The balance between automated intelligence and human intuition ensures that detection remains effective, nuanced, and contextually aware. Looking ahead, as cloud environments, IoT networks, and dispersed infrastructures redefine the boundaries of cyberspace, intrusion detection will evolve into even more predictive, adaptive, and automated forms of defense. Ultimately, their value lies not only in detecting intrusions but in fostering a culture of vigilance, resilience, and foresight, enabling societies and organizations to navigate an increasingly perilous digital realm with confidence.
Study with ExamSnap to prepare for Microsoft Certified: Azure Enterprise Data Analyst Associate Practice Test Questions and Answers, Study Guide, and a comprehensive Video Training Course. Powered by the popular VCE format, Microsoft Certified: Azure Enterprise Data Analyst Associate Certification Exam Dumps compiled by the industry experts to make sure that you get verified answers. Our Product team ensures that our exams provide Microsoft Certified: Azure Enterprise Data Analyst Associate Practice Test Questions & Exam Dumps that are up-to-date.

Microsoft Training Courses












































SPECIAL OFFER: GET 10% OFF
This is ONE TIME OFFER

A confirmation link will be sent to this email address to verify your login. *We value your privacy. We will not rent or sell your email address.
Download Free Demo of VCE Exam Simulator
Experience Avanset VCE Exam Simulator for yourself.
Simply submit your e-mail address below to get started with our interactive software demo of your free trial.