Use VCE Exam Simulator to open VCE files

Get 100% Latest Microsoft Certified: Azure Solutions Architect Expert Practice Tests Questions, Accurate & Verified Answers!
30 Days Free Updates, Instant Download!
AZ-305 Premium Bundle

Microsoft Certified: Azure Solutions Architect Expert Certification Practice Test Questions, Microsoft Certified: Azure Solutions Architect Expert Exam Dumps
ExamSnap provides Microsoft Certified: Azure Solutions Architect Expert Certification Practice Test Questions and Answers, Video Training Course, Study Guide and 100% Latest Exam Dumps to help you Pass. The Microsoft Certified: Azure Solutions Architect Expert Certification Exam Dumps & Practice Test Questions in the VCE format are verified by IT Trainers who have more than 15 year experience in their field. Additional materials include study guide and video training course designed by the ExamSnap experts. So if you want trusted Microsoft Certified: Azure Solutions Architect Expert Exam Dumps & Practice Test Questions, then you have come to the right place Read More.
Become a Microsoft Azure Solutions Architect Expert: Laying the Foundation for a Thriving Career
In the ever-evolving landscape of technology, the role of a Microsoft Azure Solutions Architect has emerged as one of the most pivotal positions in the cloud computing domain. Organizations across industries are increasingly migrating their operations to cloud platforms to achieve scalability, operational efficiency, and enhanced security. This paradigm shift has created an imperative need for professionals who can design, implement, and manage sophisticated cloud solutions tailored to specific business requirements. A Microsoft Azure Solutions Architect embodies this capability, blending technical acumen with strategic foresight to craft architectures that not only address current organizational demands but are also adaptable to future growth.
The significance of this role extends beyond mere technical implementation. Architects are entrusted with bridging the gap between business objectives and technological solutions. They analyze organizational needs, anticipate potential bottlenecks, and ensure that the infrastructure supports both performance and compliance goals. The role demands a unique combination of analytical prowess, creative problem-solving, and an in-depth understanding of cloud services. Professionals in this capacity are not merely implementers; they are visionaries who foresee how technology can transform business processes and drive innovation.
Embarking on a journey to become a Microsoft Azure Solutions Architect requires a comprehensive understanding of core cloud concepts and infrastructure principles. One of the first competencies to master is the breadth of Azure services and how they interact within a complex environment. Familiarity with virtual machines, storage accounts, databases, and networking components is essential. Beyond knowledge of individual services, a proficient architect understands how to integrate these components to form cohesive, resilient, and secure architectures.
A key aspect of this role involves developing a mindset oriented toward continuous learning. The cloud landscape is in constant flux, with new services, updates, and best practices emerging regularly. Aspiring architects must cultivate an intellectual agility that allows them to absorb new knowledge, experiment with innovative solutions, and adapt existing strategies to evolving technological landscapes. Participation in professional communities, attendance at webinars, and exploration of real-world case studies are invaluable approaches to honing this adaptability.
Analytical thinking and strategic foresight are complementary skills that further strengthen foundational competence. Architects must be able to dissect business requirements, identify critical dependencies, and anticipate potential risks. This involves not only technical analysis but also evaluating operational, financial, and regulatory implications. The ability to align cloud solutions with broader organizational goals separates competent professionals from exemplary architects.
The Azure ecosystem is a vast and intricate constellation of services, tools, and frameworks. An effective architect is proficient in understanding the interdependencies within this environment and designing solutions that maximize both efficiency and scalability. Core services such as compute, storage, networking, and identity management form the backbone of Azure, and mastering their application is essential. Compute services, including virtual machines, containers, and serverless functions, provide the processing capability required to run applications, while storage solutions ensure that data is available, secure, and optimized for performance. Networking components orchestrate connectivity, access control, and traffic management, forming the critical pathways for data flow. Identity and access management services secure environments and enforce policies that comply with internal and regulatory requirements.
Beyond these foundational services, architects must develop an appreciation for the nuanced features that differentiate Azure from other cloud platforms. Features like automated scaling, load balancing, and resource monitoring enable solutions to maintain performance under varying workloads. Advanced tools such as Azure Resource Manager and policy management facilitate governance, ensuring that infrastructure remains compliant and cost-effective. By developing a holistic understanding of the ecosystem, architects can anticipate challenges and craft solutions that balance innovation, stability, and resource efficiency.
A critical aspect of becoming a Microsoft Azure Solutions Architect lies in cultivating a mindset attuned to problem-solving and innovation. Architects are frequently confronted with complex scenarios that require the synthesis of multiple technologies and methodologies. They must devise solutions that not only meet immediate business needs but also anticipate long-term implications. This entails a sophisticated understanding of trade-offs, such as balancing performance with cost or innovation with operational stability.
Creative problem-solving in this context is often informed by experiential learning. Hands-on experimentation with cloud services allows architects to explore unconventional solutions, evaluate outcomes, and refine approaches. Moreover, architects must exercise intellectual curiosity, delving into emerging technologies, architectural patterns, and industry case studies. By integrating lessons from these explorations, they can propose solutions that are both inventive and practical.
Decision-making is another critical component of the professional mindset. Architects must evaluate numerous factors, including security, compliance, cost, and system reliability. They weigh potential risks against anticipated benefits, often navigating ambiguous or incomplete information. Effective architects demonstrate decisiveness while remaining flexible enough to revise strategies in response to new insights or changing conditions.
Technical mastery alone is insufficient to excel as a Microsoft Azure Solutions Architect. Equally important is the ability to align technological decisions with broader business objectives. This involves comprehending organizational goals, market dynamics, and operational constraints. Architects serve as intermediaries between technical teams and business stakeholders, translating complex requirements into actionable design specifications.
This alignment requires both communication and analytical skills. Architects must articulate the rationale behind architectural decisions in a manner that resonates with non-technical audiences, emphasizing value creation, risk mitigation, and operational efficiency. They must also evaluate how proposed solutions impact budgets, timelines, and resource allocation. By consistently aligning technology with strategy, architects ensure that cloud initiatives deliver tangible business benefits and maintain organizational resilience.
To establish a robust foundation, aspiring architects should embark on a structured learning path that integrates theoretical knowledge with practical experience. Initial exposure to Azure fundamentals introduces core concepts, terminology, and service categories. Subsequent exploration of more advanced topics, such as solution design, automation, and security best practices, enables the development of comprehensive architectural competencies.
Practical experience is indispensable. Engaging in real-world projects, sandbox environments, or proof-of-concept deployments fosters a deep understanding of how services interact and how design decisions influence performance and reliability. Exposure to diverse scenarios enhances problem-solving skills, allowing architects to anticipate challenges and devise effective solutions. Participation in open-source initiatives or collaborative community projects further amplifies experiential learning, promoting knowledge exchange and the refinement of technical proficiency.
An architect's effectiveness is closely tied to analytical rigor and strategic foresight. Analytical skills allow professionals to dissect complex systems, identify bottlenecks, and evaluate potential improvements. They assess system performance, security posture, and compliance adherence, drawing insights that inform design modifications. Strategic acumen complements analysis by situating technical decisions within a broader organizational context, ensuring that architecture supports long-term objectives and sustainable growth.
This dual focus on analysis and strategy is essential for navigating the multifaceted challenges inherent in cloud environments. Architects must reconcile competing priorities, such as maximizing performance while minimizing costs or ensuring security without hindering usability. The ability to make informed decisions amidst such complexity distinguishes accomplished professionals in the field.
Cloud security and compliance are integral aspects of solution architecture. Architects must possess a nuanced understanding of regulatory frameworks, including data protection mandates and industry-specific standards. They implement measures such as identity management, encryption, access controls, and continuous monitoring to safeguard sensitive information. Security is not merely a reactive measure but a proactive design principle embedded throughout the architecture.
Maintaining compliance requires continuous vigilance. Architects monitor updates to regulations, assess the impact on existing systems, and implement changes to ensure adherence. This proactive approach mitigates risk, protects organizational assets, and fosters trust among stakeholders. Knowledge of security frameworks, risk assessment methodologies, and industry best practices enables architects to integrate robust protections seamlessly into their solutions.
Finally, professional growth as an architect is reinforced through active engagement in the broader Azure community. Participating in user groups, forums, and industry events provides exposure to emerging trends, shared experiences, and innovative practices. Networking with peers and experts fosters collaboration, mentorship, and the exchange of ideas, which can accelerate learning and professional development.
Engagement extends beyond passive observation. Architects who contribute to discussions, present case studies, or share practical insights enhance their visibility and credibility. This reciprocal involvement cultivates both personal growth and collective advancement within the cloud computing domain, reinforcing the interconnected nature of learning, experience, and professional success.
The journey of a Microsoft Azure Solutions Architect advances significantly once foundational knowledge has been established. At this stage, professionals focus on designing sophisticated architectures that balance performance, reliability, and cost efficiency. Understanding the intricate interactions between compute, storage, and networking services is essential for creating solutions that withstand the dynamic demands of modern enterprises. Architects consider factors such as workload distribution, failover strategies, and system resilience while integrating Azure’s wide array of services to optimize performance and maintain operational stability.
Solution design demands a meticulous approach that weighs trade-offs between speed, scalability, and resource utilization. Architects frequently evaluate scenarios where performance might conflict with budgetary constraints or where new features could introduce unanticipated risks. The capacity to model these complex interdependencies and anticipate operational challenges is what distinguishes highly effective architects. They use a combination of analytical rigor, scenario planning, and iterative refinement to ensure solutions not only meet current needs but remain adaptable to future requirements.
Security and compliance constitute a central pillar in advanced architectural design. Microsoft Azure Solutions Architects must implement robust strategies to safeguard data and applications while ensuring adherence to regulatory standards. This involves establishing multi-layered security measures, including identity management, role-based access controls, encryption protocols, and continuous monitoring systems. Architects are expected to maintain vigilance over potential vulnerabilities and proactively integrate mitigation strategies into every aspect of the architecture.
Beyond reactive measures, architects engage in proactive governance by regularly reviewing security policies, auditing systems, and updating controls to comply with frameworks such as GDPR, HIPAA, and industry-specific regulations. Understanding the subtle distinctions between compliance requirements allows architects to design systems that meet legal obligations without compromising operational efficiency. This expertise ensures that sensitive information remains protected and that organizations can confidently scale operations in the cloud while mitigating risk.
Security awareness extends to incident response planning and risk assessment. Architects establish procedures for detecting, analyzing, and addressing potential breaches. They leverage Azure-native tools to automate monitoring, generate alerts, and maintain logs for forensic and compliance purposes. This comprehensive approach to security fosters resilience, instills stakeholder confidence, and forms a cornerstone of a high-functioning cloud architecture.
In contemporary cloud environments, the integration of DevOps practices and automation is indispensable. Azure Solutions Architects play a critical role in bridging development and operations teams, ensuring that deployments are reliable, consistent, and scalable. Infrastructure as Code methodologies allow architects to define and manage infrastructure programmatically, enabling repeatable and auditable deployments. Continuous integration and continuous deployment pipelines streamline the release process, reducing the likelihood of errors and accelerating time-to-market for new features.
Automation extends beyond deployment, encompassing testing, monitoring, and configuration management. Architects design processes that automatically validate code, assess system performance, and maintain compliance standards. This level of automation enhances operational efficiency, fosters innovation, and reduces manual intervention. By implementing such practices, architects create an environment where both development and operations can function seamlessly while maintaining high standards of quality and security.
Cultural adaptation is also a critical consideration in implementing DevOps strategies. Architects must guide teams through shifts in workflow, address resistance to new methodologies, and promote a mindset of continuous improvement. Success in these endeavors requires clear communication, training programs, and iterative feedback mechanisms to ensure alignment with organizational goals.
A defining competency of an accomplished Azure Solutions Architect is the ability to ensure that solutions scale efficiently while maintaining high performance. Architects evaluate workload patterns, anticipate peak demand, and implement mechanisms to distribute computational load effectively. Techniques such as horizontal scaling, load balancing, and caching strategies enable systems to respond dynamically to fluctuating demand without compromising performance.
In parallel, architects focus on cost-conscious resource management. Azure provides tools that allow architects to monitor utilization, predict consumption trends, and optimize resource allocation. Intelligent scaling, serverless architectures, and pay-as-you-go models contribute to efficient resource utilization, enabling organizations to maximize performance while controlling expenditures.
Regular performance assessment is crucial. Architects conduct stress testing, monitor application response times, and analyze resource bottlenecks to identify opportunities for improvement. By continuously optimizing performance, architects ensure that systems remain responsive, resilient, and capable of supporting evolving business requirements.
Modern enterprises rely heavily on the effective management of data, and architects must design systems that support secure, efficient, and reliable data handling. Azure’s diverse data services, including relational and non-relational databases, data lakes, and analytics platforms, offer versatile options for storing and processing information. Architects must select appropriate solutions based on the volume, velocity, and variety of data, ensuring seamless integration with applications and operational workflows.
Data integration involves orchestrating data pipelines, automating ETL processes, and implementing governance frameworks to maintain data integrity and quality. Architects also focus on redundancy and disaster recovery strategies to protect against data loss and ensure business continuity. The ability to harmonize disparate data sources, enforce security controls, and enable analytics at scale is a hallmark of advanced architectural proficiency.
A robust architecture is not only about initial deployment but also about ongoing observability and maintenance. Architects implement monitoring solutions to track system performance, detect anomalies, and provide insights for continuous improvement. Metrics, logging, and alerting mechanisms allow teams to respond rapidly to incidents and optimize operations proactively.
Azure provides integrated tools that allow architects to visualize infrastructure health, assess application performance, and anticipate potential failures. By leveraging these tools, architects can maintain high availability, minimize downtime, and deliver reliable experiences to end users. Observability practices also support compliance objectives, ensuring that operational activities are documented and auditable.
Staying ahead in cloud architecture requires architects to be conversant with emerging technologies and novel architectural patterns. Concepts such as microservices, serverless computing, and container orchestration enable flexible, modular solutions that can adapt to shifting business landscapes. Architects explore these approaches in the context of Azure, evaluating their applicability, potential risks, and operational implications.
Innovation is guided by strategic thinking. Architects assess the business value of new technologies, weighing benefits against cost, security, and maintainability. By thoughtfully incorporating innovative elements, architects enhance system capabilities while maintaining the stability and reliability essential for enterprise operations.
Advanced architectural responsibilities often extend beyond technical execution to include collaboration and leadership. Architects must coordinate cross-functional teams, mediate between technical and business stakeholders, and mentor junior engineers. Effective communication is vital for translating complex technical concepts into actionable insights and ensuring that all parties share a common understanding of objectives and constraints.
Leadership in architecture also involves fostering a culture of continuous learning and quality improvement. By setting standards, defining best practices, and promoting knowledge sharing, architects influence organizational capability and elevate the overall quality of cloud solutions. Their guidance ensures that teams adhere to governance, security, and operational policies while encouraging innovation and experimentation.
A critical aspect of advanced architectural practice is the ability to anticipate and mitigate risk. Architects evaluate potential vulnerabilities, plan for disaster recovery, and design failover mechanisms to maintain operational continuity. This strategic foresight enables organizations to navigate uncertainties and respond effectively to evolving threats.
Financial and operational risk considerations are integrated into architectural decisions. Architects assess the implications of design choices on cost, resource allocation, and scalability. They plan for contingencies, prioritize investments in resilient infrastructure, and establish monitoring systems to detect deviations from expected performance. This proactive approach strengthens the organization’s capacity to withstand disruptions while optimizing return on investment.
Even at an advanced level, learning remains an integral part of an architect’s professional journey. Engaging with professional communities, attending workshops, and following thought leadership within the cloud domain ensures that architects remain at the forefront of technological innovation. Hands-on experimentation, certification updates, and exposure to new case studies contribute to maintaining proficiency and expanding expertise.
Exposure to peer networks and collaborative initiatives provides valuable insights into novel strategies, real-world challenges, and emerging best practices. By remaining intellectually agile, architects can adapt to changing requirements, incorporate innovative techniques, and continuously refine their design approaches to deliver solutions that are resilient, scalable, and secure.
Embarking on the journey to attain formal recognition as a Microsoft Azure Solutions Architect requires a strategic approach to certification. Certifications validate both theoretical knowledge and practical expertise, offering a credible benchmark of competence in designing and implementing cloud solutions. The foundational certification, often pursued first, introduces the core concepts of cloud computing, including the breadth of Azure services, basic security practices, and infrastructure management. Completing this certification provides a structured understanding of the Azure ecosystem, equipping professionals with the confidence to explore more advanced concepts.
Progressing to advanced certification demonstrates the ability to architect sophisticated solutions. Candidates must exhibit proficiency in designing, deploying, and managing complex cloud infrastructures while considering compute, storage, networking, and security requirements. Certification preparation often involves extensive study, practice exams, and hands-on experimentation, ensuring that architects can apply principles to real-world scenarios. Attaining these credentials enhances professional credibility and opens doors to opportunities that require both strategic insight and technical mastery.
Certification also encourages continual engagement with evolving technologies. Architects remain updated on new services, features, and best practices, aligning their skills with industry standards. The pursuit of these credentials is not merely an academic exercise but a commitment to ongoing professional development and excellence in cloud architecture.
While certification establishes foundational knowledge, practical experience is indispensable in developing true mastery. Engaging in real-world projects allows architects to translate theoretical understanding into actionable solutions. These projects often involve designing end-to-end architectures, integrating multiple Azure services, and ensuring performance, security, and scalability are maintained. Working collaboratively on complex deployments enhances problem-solving capabilities and exposes architects to the intricacies of enterprise environments, where unforeseen challenges frequently arise.
Azure provides sandbox environments and free-tier offerings that allow professionals to experiment without impacting production systems. These resources enable hands-on learning, allowing architects to simulate deployments, test automation strategies, and evaluate the effectiveness of security and monitoring practices. Utilizing these environments fosters intellectual agility and a deep comprehension of how individual components interact within the broader ecosystem.
Participation in open-source projects further enriches practical expertise. Contributing to community initiatives, whether by coding, reviewing infrastructure configurations, or providing feedback, enhances understanding of best practices while promoting collaborative learning. Architects who actively engage in these projects gain exposure to diverse approaches, broaden their skill set, and demonstrate their capabilities to peers and potential employers.
A distinguishing characteristic of accomplished Microsoft Azure Solutions Architects is a commitment to lifelong learning. The cloud computing landscape evolves rapidly, and architects must consistently assimilate new knowledge to remain relevant. This involves attending webinars, workshops, and online courses that introduce emerging technologies, architectural patterns, and operational strategies. Engaging with authoritative blogs, technical publications, and professional forums ensures that architects remain informed about trends, best practices, and case studies that reflect practical applications.
Professional networking and community engagement amplify learning opportunities. Interacting with peers, mentors, and industry experts provides insights that extend beyond formal education. Architects can exchange experiences, solicit advice on complex problems, and gain exposure to innovative techniques. By integrating these insights with hands-on experimentation, architects refine their understanding and develop nuanced approaches to solution design and implementation.
Renewing and expanding certifications is also a critical component of continuous learning. Advanced certifications in security, data management, and application development provide specialized knowledge that enhances an architect’s ability to address diverse organizational requirements. Maintaining current certifications ensures alignment with evolving standards and reinforces professional credibility.
Mentorship plays a pivotal role in skill advancement. Experienced architects who guide less seasoned professionals facilitate the transfer of knowledge, promote adherence to best practices, and cultivate problem-solving abilities. Mentorship can occur in formal settings, such as structured programs, or informally through collaborative project work. The exchange of perspectives encourages critical thinking, exposes mentees to novel approaches, and fosters professional growth for both mentor and mentee.
Knowledge transfer extends to organizational practices. Architects often develop documentation, guidelines, and reference architectures that standardize processes and promote consistency across teams. Sharing expertise in this manner ensures that institutional knowledge is preserved and that emerging professionals can build upon proven strategies. This cyclical process of mentorship and knowledge dissemination reinforces a culture of continuous improvement within the cloud environment.
Effective architects leverage advanced Azure tools to enhance efficiency and reliability. Automation is a core strategy, encompassing the deployment, monitoring, and maintenance of resources. By utilizing Infrastructure as Code, architects can define infrastructure in a reproducible and auditable manner, reducing human error and accelerating deployment cycles. Automated testing and monitoring frameworks further ensure that solutions meet performance, compliance, and security standards consistently.
The integration of advanced tools extends to orchestration and resource optimization. Architects monitor resource consumption, analyze utilization patterns, and adjust configurations to balance cost and performance. These practices are critical in dynamic environments where workloads fluctuate and operational demands evolve rapidly. Mastery of such tools enables architects to deliver solutions that are both resilient and cost-effective, providing tangible value to organizations.
Participation in open-source initiatives cultivates both technical skill and professional visibility. Architects who contribute to community projects gain experience with real-world scenarios and diverse architectural patterns. Engagement can take many forms, including submitting code, providing documentation, reviewing infrastructure configurations, or reporting and addressing issues. These activities strengthen familiarity with Azure services, enhance problem-solving capabilities, and create a portfolio of practical achievements.
Community involvement also fosters a collaborative mindset. Architects exchange insights, adopt innovative approaches, and stay informed about industry trends. This engagement cultivates a network of peers and mentors, creating avenues for learning and professional growth that extend beyond organizational boundaries. The combined effect of hands-on experience and community participation accelerates the development of expertise, ensuring that architects remain adaptable and proficient in an evolving technological landscape.
A structured learning roadmap helps architects systematically acquire knowledge and practical experience. Initial phases focus on mastering core Azure services and infrastructure, followed by advanced exploration of automation, security, and governance practices. Hands-on experimentation, coupled with project-based application, reinforces conceptual understanding. Regular assessment through self-evaluation, peer feedback, and formal certification exams ensures progress and identifies areas for refinement.
Integrating continuous learning with practical application fosters deep comprehension. Architects who embrace iterative learning cycles—combining study, experimentation, and reflection—develop robust expertise that enables them to tackle increasingly complex challenges with confidence. A disciplined roadmap also facilitates strategic career progression, ensuring that each learning endeavor aligns with long-term professional goals.
Intellectual agility is an invaluable trait for Microsoft Azure Solutions Architects. The ability to assimilate new information rapidly, adapt to shifting requirements, and apply innovative solutions is essential in a field characterized by rapid technological evolution. Architects cultivate this agility by embracing diverse learning modalities, exploring unconventional solutions, and continuously challenging assumptions.
Exposure to emerging architectural patterns, cloud-native design philosophies, and evolving security practices strengthens cognitive flexibility. Architects who actively experiment with new tools, services, and methodologies develop an intuitive understanding of how components interact and how to optimize their deployment. This agility not only enhances problem-solving capabilities but also positions architects to anticipate trends, seize opportunities, and implement forward-looking solutions.
Collaboration across teams is critical for skill advancement. Architects engage with development, operations, security, and business units to ensure solutions are coherent, efficient, and aligned with organizational goals. Cross-functional learning provides exposure to diverse perspectives, revealing how technical decisions impact performance, cost, and user experience. Architects integrate these insights into architectural designs, fostering systems that are resilient, adaptable, and value-driven.
Mentorship and knowledge sharing extend the benefits of collaboration. By teaching, guiding, and reviewing the work of colleagues, architects reinforce their own understanding while elevating team capabilities. This reciprocal process of learning and teaching contributes to the collective advancement of organizational expertise in cloud architecture.
Maintaining a comprehensive portfolio is crucial for demonstrating expertise and tracking professional growth. Architects document projects, solutions designed, and contributions to community initiatives, creating a tangible record of experience. Portfolios serve multiple purposes: they highlight technical proficiency, illustrate problem-solving capabilities, and provide evidence of continuous learning.
Portfolios also function as a reflective tool. By reviewing past projects, architects can identify areas for improvement, recognize recurring patterns, and refine design strategies. This practice encourages intentional development, reinforcing the integration of practical experience with theoretical knowledge. A well-curated portfolio not only enhances career prospects but also provides a reference framework for future architectural endeavors.
Navigating Rapid Technological Evolution
The landscape of cloud computing is in perpetual motion, and Microsoft Azure Solutions Architects must adeptly navigate constant technological evolution. Services are continuously updated, new tools are introduced, and best practices are refined at a brisk pace. Architects must develop the intellectual agility to absorb these changes, evaluate their implications, and implement adjustments that maintain operational excellence. Staying current involves more than cursory awareness; it demands deliberate engagement with release notes, technical documentation, webinars, and industry thought leadership to anticipate shifts that may affect architecture, security, or performance.
Continuous adaptation also requires a mindset that embraces experimentation and iterative learning. Architects deploy test environments, simulate real-world scenarios, and explore innovative approaches before integrating changes into production systems. This proactive methodology ensures that solutions remain resilient and efficient despite an ever-shifting technological milieu, allowing organizations to derive maximum value from their cloud investments.
One of the most nuanced challenges facing architects is the equilibrium between innovation and operational stability. Introducing novel technologies can enhance efficiency, scalability, or user experience, but untested features may compromise reliability or compliance. Effective architects rigorously evaluate the trade-offs between experimentation and stability, incorporating mechanisms for risk mitigation, monitoring, and rollback.
They implement strategies such as incremental deployment, feature flagging, and sandbox testing to minimize disruption. Regular performance assessments and scenario analyses allow architects to anticipate potential failures and adjust systems proactively. Balancing these competing priorities requires foresight, meticulous planning, and the capacity to communicate implications to both technical teams and organizational stakeholders. Architects who master this equilibrium are able to drive innovation without jeopardizing operational integrity, ensuring that progress and reliability coexist harmoniously.
Efficient resource management is another cornerstone of successful architecture. Microsoft Azure Solutions Architects must ensure that systems are not only performant but also cost-effective. This involves continuous monitoring of resource utilization, intelligent provisioning, and strategic allocation of virtual machines, storage accounts, and networking resources. By rightsizing deployments and leveraging pay-as-you-go models, architects can prevent overprovisioning while maintaining scalability and responsiveness.
Architects also evaluate long-term expenditure patterns and implement predictive budgeting strategies. Techniques such as reserving instances for predictable workloads, automating resource deallocation during periods of low demand, and analyzing usage patterns contribute to financial prudence without compromising service quality. Effective cost management reinforces organizational efficiency, allowing businesses to reinvest savings into innovation and growth initiatives.
Performance optimization is inseparable from architectural excellence. Architects analyze system behavior under variable workloads, identify bottlenecks, and deploy techniques such as horizontal scaling, caching, and load balancing to maintain responsiveness. These strategies ensure that applications remain accessible, reliable, and capable of handling sudden surges in demand.
In parallel, architects leverage monitoring and observability tools to gain granular insights into system performance. Metrics, logs, and alerts provide actionable intelligence that informs adjustments, capacity planning, and predictive maintenance. This continuous attention to performance fosters operational resilience, enabling organizations to deliver seamless experiences to users while accommodating growth and expansion.
Advanced architectural responsibility encompasses rigorous security and compliance management. Architects embed security considerations throughout solution design, employing measures such as multi-layered access control, encryption of data at rest and in transit, and automated monitoring for suspicious activities. Compliance adherence is maintained through ongoing evaluation of regulatory frameworks, ensuring that systems meet standards for data protection, privacy, and industry-specific mandates.
Proactive security practices extend to incident response planning and vulnerability assessments. Architects design protocols for detecting, analyzing, and remediating potential threats, reducing the likelihood of breaches and mitigating potential damage. By integrating security as a foundational principle rather than a reactive measure, architects create environments that are resilient, trustworthy, and aligned with organizational and regulatory expectations.
Long-term success requires architects to cultivate professional visibility and influence. Engaging with industry forums, user groups, and conferences provides platforms for sharing insights, learning from peers, and establishing thought leadership. Presenting case studies, contributing to technical discussions, and mentoring emerging professionals strengthens credibility and positions architects as authoritative voices within the cloud computing community.
Professional visibility also supports career progression by expanding networks, revealing collaborative opportunities, and facilitating recognition for innovative solutions. Architects who invest in building a personal brand through knowledge sharing, community engagement, and demonstrable expertise enhance their career prospects while contributing to the collective advancement of their field.
Leadership is an intrinsic aspect of the architect’s role. Microsoft Azure Solutions Architects frequently coordinate diverse teams spanning development, operations, security, and business units. Effective leadership involves articulating architectural vision, aligning teams with strategic objectives, and fostering collaboration. By encouraging open communication, knowledge exchange, and shared responsibility, architects cultivate an environment where innovation and operational excellence coexist.
Cross-functional collaboration also reinforces holistic solution design. Architects integrate perspectives from different disciplines to anticipate challenges, address user needs, and align technology with organizational priorities. This inclusive approach ensures that cloud solutions are not only technically robust but also attuned to the broader business context, enhancing adoption, usability, and impact.
Comprehensive documentation is critical for maintaining system integrity and facilitating knowledge transfer. Architects create detailed records of architecture designs, deployment procedures, and operational guidelines, ensuring that critical information is preserved for future teams. Documentation also supports compliance audits, risk assessments, and troubleshooting activities, serving as both a reference and a strategic asset.
Knowledge management extends beyond static documentation. Architects cultivate repositories of best practices, lessons learned, and reusable components that promote efficiency and consistency across projects. This repository fosters a culture of continuous improvement, enabling teams to build on prior successes while avoiding repetitive errors.
Remaining attuned to emerging trends is essential for sustained relevance. Architects explore innovations such as serverless computing, containerization, artificial intelligence integration, and advanced analytics to expand the capabilities of cloud solutions. By evaluating these technologies in the context of organizational needs, architects can judiciously incorporate them to enhance performance, reduce complexity, or enable new functionalities.
A discerning approach to emerging technologies balances novelty with proven practices. Architects assess potential benefits, operational impact, and integration complexity before adoption. This careful evaluation ensures that innovation contributes to sustainable growth, operational efficiency, and strategic advantage rather than introducing instability or unnecessary risk.
Long-term impact is amplified when architects mentor peers and disseminate knowledge. Guiding less experienced professionals, conducting workshops, and contributing to internal training programs promote skill development across teams. Mentorship reinforces the architect’s own expertise, sharpens leadership abilities, and cultivates a collaborative culture that enhances organizational capability.
Sharing insights through presentations, publications, and community engagement extends influence beyond the immediate workplace. Architects who actively contribute to knowledge dissemination help shape industry standards, foster professional networks, and inspire the next generation of cloud specialists. This reciprocal cycle of learning, teaching, and innovation strengthens both personal and organizational growth.
Sustaining a long-term career as a Microsoft Azure Solutions Architect requires continuous professional development. Architects proactively seek opportunities to refine skills, explore advanced certifications, and engage in challenging projects. They balance hands-on technical work with strategic planning, leadership, and community involvement, creating a multifaceted professional profile that is resilient to shifts in technology and industry demands.
Adaptability is a hallmark of sustainable career growth. Architects who cultivate flexibility, maintain curiosity, and embrace continuous improvement remain relevant despite the rapid evolution of cloud technologies. Their capacity to anticipate trends, integrate emerging tools, and guide organizations through transformation positions them as indispensable assets in any enterprise pursuing cloud adoption or modernization.
Becoming a Microsoft Azure Solutions Architect requires a harmonious integration of technical expertise, strategic insight, and continuous professional growth. The journey begins with mastering the core Azure services and infrastructure, developing a deep understanding of solution design principles, cloud security, and compliance. Practical experience through real-world projects, sandbox experimentation, and contributions to community initiatives solidifies knowledge and hones problem-solving skills.
Certifications serve as benchmarks for credibility, validating both theoretical understanding and applied proficiency. Achieving foundational and advanced credentials ensures that architects are equipped to design, deploy, and manage complex cloud solutions while adhering to best practices and regulatory requirements. Continuous learning, through webinars, workshops, publications, and professional networks, enables architects to stay abreast of technological advancements, emerging trends, and evolving operational standards.
Advanced architectural responsibilities extend to optimizing performance, scalability, and cost management. Architects implement intelligent resource allocation, monitoring, and automation strategies to maintain reliability, efficiency, and financial prudence. Security is embedded throughout every layer of the architecture, with multi-layered access controls, encryption, proactive monitoring, and compliance alignment ensuring that systems remain resilient and trustworthy.
Intellectual agility, strategic foresight, and the ability to balance innovation with operational stability distinguish exceptional architects. They navigate rapid technological evolution, integrate emerging tools thoughtfully, and anticipate organizational needs, ensuring solutions remain adaptable and forward-looking. Leadership and collaboration are central, as architects coordinate cross-functional teams, mentor peers, and foster knowledge-sharing cultures that elevate collective expertise.
Documenting achievements, maintaining a comprehensive portfolio, and engaging with the wider professional community enhance visibility, credibility, and influence. These practices, combined with reflective learning and iterative experimentation, strengthen problem-solving abilities and support long-term career sustainability. Architects who cultivate these competencies are prepared to deliver transformative, resilient, and efficient cloud solutions that drive organizational growth, operational excellence, and innovation.
Ultimately, success as a Microsoft Azure Solutions Architect emerges from the synergy of hands-on experience, continuous learning, strategic vision, and collaborative engagement. By embracing these principles, architects position themselves as invaluable assets in the evolving cloud landscape, capable of shaping organizational capabilities and contributing meaningfully to the future of technology.
Study with ExamSnap to prepare for Microsoft Certified: Azure Solutions Architect Expert Practice Test Questions and Answers, Study Guide, and a comprehensive Video Training Course. Powered by the popular VCE format, Microsoft Certified: Azure Solutions Architect Expert Certification Exam Dumps compiled by the industry experts to make sure that you get verified answers. Our Product team ensures that our exams provide Microsoft Certified: Azure Solutions Architect Expert Practice Test Questions & Exam Dumps that are up-to-date.

Microsoft Training Courses


















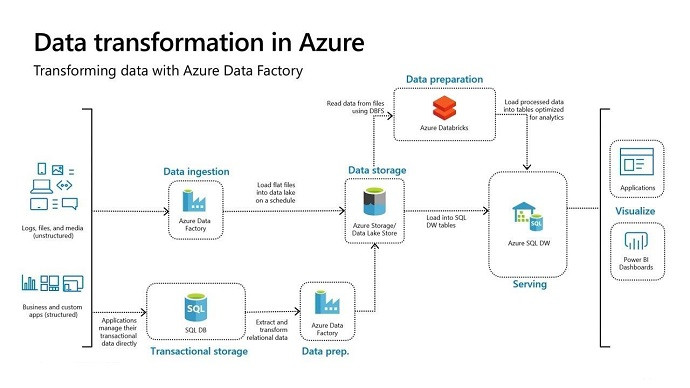


























SPECIAL OFFER: GET 10% OFF
This is ONE TIME OFFER

A confirmation link will be sent to this email address to verify your login. *We value your privacy. We will not rent or sell your email address.
Download Free Demo of VCE Exam Simulator
Experience Avanset VCE Exam Simulator for yourself.
Simply submit your e-mail address below to get started with our interactive software demo of your free trial.